This is the Continuous Integration Build of FHIR (will be incorrect/inconsistent at times).
See the Directory of published versions 
Responsible Owner: Security  Work Group Work Group | Normative | Security Category: Not Classified | Compartments: Device, Group, Patient, Practitioner |
A record of an event relevant for purposes such as operations, privacy, security, maintenance, and performance analysis.
The audit event is based on the IHE-ATNA Audit record definitions  , originally from RFC 3881
, originally from RFC 3881  , and now managed by
DICOM (see DICOM Part 15 Annex A5
, and now managed by
DICOM (see DICOM Part 15 Annex A5  ).
).
This resource is managed collaboratively between HL7, DICOM, and IHE.
A record of an event relevant for purposes such as operations, privacy, security, maintenance, and performance analysis.
All actors - such as applications, processes, and services - involved in an auditable event SHOULD record an AuditEvent. This will likely result in multiple AuditEvent entries that show whether privacy and security safeguards, such as access control, are properly functioning across an enterprise's system-of-systems. Thus, it is typical to get an auditable event recorded by both the application in a workflow process and the servers that support them. For this reason, duplicate entries are expected, which is helpful because it MAY aid in the detection of security, privacy, or other operational problems. For example, fewer than expected actors being recorded in a multi-actor process or attributes related to those records being in conflict, which is an indication of a security problem. There MAY be non-participating actors, such as trusted intermediary, that also detect a security, privacy, or operational relevant event and thus would record an AuditEvent.
Security relevant events are not limited to communications or RESTful events. They include:
See the Audit Event Category vocabulary for guidance on some security relevant event categories.
The AuditEvent resource holds the details of an event in terms of who, what, where, when, and why. Where the identification of the who participated is the agent. An agent can be a person, an organization, software, device, or other actors that MAY be ascribed responsibility. What objects were used/created/updated is recorded as the entity. An entity is an identifiable physical, digital, conceptual or other kind of thing; entities MAY be real or imaginary.
The content of an AuditEvent is primarily intended for administrative use; used by security system administrators, security and privacy information managers, records management personnel, etc. The AuditEvent MAY also inform the Patient about uses of their data. This content can be accessible or used directly by other healthcare users, such as providers or patients for gaining insight into who and what has been done. The AuditEvent record includes very sensitive information so access to the AuditEvent would be highly privileged and controlled. For example, when providing AuditEvent to a patient the data feed would be limited to the Patient compartment, and the content MAY be subsetted or masked in order to meet privacy needs. The AuditEvent record is not intended to replace other audit logs, but rather used to enhance them, or to be used as an API to many audit logs.
Relationship of AuditEvent and Provenance resources are often (though not exclusively) created by the application responding to the create/read/query/update/delete/execute etc. event. A Provenance resource contains overlapping information, but is a record-keeping assertion that gathers information about the context in which the information in a resource "came to be" in its current state, e.g., whether it was created de novo or obtained from another entity in whole, part, or by transformation. Provenance resources are prepared by the application that initiates the create/update of the resource and MAY be persisted with the AuditEvent target resource.
Structure
| Name | Flags | Card. | Type | Description & Constraints Filter:   |
|---|---|---|---|---|
 |
N | DomainResource | Record of an event Elements defined in Ancestors: id, meta, implicitRules, language, text, contained, extension, modifierExtension | |
  |
Σ | 1..1 | CodeableConcept | High level categorization of audit event Binding: Example Audit Event ID (Example) |
  |
Σ | 0..* | CodeableConcept | Specific type of event Binding: Example Audit Event Sub-Type (Example) |
  |
Σ | 0..1 | code | Type of action performed during the event Binding: Audit Event Action (Required) |
  |
Σ | 0..1 | code | emergency | alert | critical | error | warning | notice | informational | debug Binding: Audit Event Severity (Required) |
  |
0..1 | When the activity occurred | ||
   |
Period | |||
  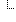 |
dateTime | |||
  |
Σ | 1..1 | instant | Time when the event was recorded |
  |
Σ | 0..1 | BackboneElement | Whether the event succeeded or failed |
   |
Σ | 1..1 | Coding | Whether the event succeeded or failed Binding: Example Audit Event Outcome (Preferred) |
  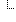 |
Σ | 0..* | CodeableConcept | Additional outcome detail Binding: Example Audit Event Outcome Detail (Example) |
  |
Σ | 0..* | CodeableConcept | Authorization related to the event Binding: PurposeOfUse  (Example) (Example) |
  |
0..* | Reference(Any) | Workflow authorization within which this event occurred | |
  |
Σ | 0..1 | Reference(Patient) | The patient is the subject of the data used/created/updated/deleted during the activity |
  |
0..1 | Reference(Encounter) | Encounter within which this event occurred or which the event is tightly associated | |
  |
Σ | 1..* | BackboneElement | Actor involved in the event |
   |
0..1 | CodeableConcept | How agent participated Binding: Participation Role Type (Preferred) | |
   |
0..* | CodeableConcept | Agent role in the event Binding: Example Security Role Type (Example) | |
   |
Σ | 1..1 | Reference(Practitioner | PractitionerRole | Organization | CareTeam | Patient | Device | DeviceDefinition | RelatedPerson | Group | HealthcareService) | Identifier of who |
   |
Σ | 0..1 | boolean | Whether user is initiator |
   |
0..1 | Reference(Location) | The agent location when the event occurred | |
   |
0..* | uri | Policy that authorized the agent participation in the event | |
   |
0..1 | This agent network location for the activity | ||
    |
Reference(Endpoint) | |||
    |
uri | |||
   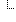 |
string | |||
  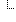 |
0..* | CodeableConcept | Allowable authorization for this agent Binding: PurposeOfUse  (Example) (Example) | |
  |
Σ | 1..1 | BackboneElement | Audit Event Reporter |
   |
0..1 | Reference(Location) | Logical source location within the enterprise | |
   |
Σ | 1..1 | Reference(Practitioner | PractitionerRole | Organization | CareTeam | Patient | Device | RelatedPerson) | The identity of source detecting the event |
   |
0..* | CodeableConcept | The type of source where event originated Binding: Audit Event Source Type (Preferred) | |
  |
Σ | 0..* | BackboneElement | Data or objects used |
   |
Σ | 0..1 | Reference(Any) | Specific instance of resource |
   |
0..1 | CodeableConcept | What role the entity played Binding: Example Audit Event Entity Role (Example) | |
   |
0..* | CodeableConcept | Security labels on the entity Binding: Example set of Security Labels (Example) | |
   |
0..1 | string | Descriptive text | |
   |
Σ | 0..1 | base64Binary | Query parameters |
   |
0..* | BackboneElement | Additional Information about the entity | |
    |
1..1 | CodeableConcept | The name of the extra detail property Binding: Example value set Audit Event Entity Detail Type (Example) | |
    |
1..1 | Property value | ||
     |
Quantity | |||
     |
CodeableConcept | |||
     |
string | |||
     |
boolean | |||
     |
integer | |||
     |
Range | |||
     |
Ratio | |||
     |
time | |||
     |
dateTime | |||
     |
Period | |||
     |
base64Binary | |||
   |
0..* | see agent | Entity is attributed to this agent | |
 Documentation for this format Documentation for this format  | ||||
See the Extensions for this resource
UML Diagram (Legend)
XML Template
<AuditEvent xmlns="http://hl7.org/fhir"><!-- from Resource: id, meta, implicitRules, and language --> <!-- from DomainResource: text, contained, extension, and modifierExtension --> <type><!-- 1..1 CodeableConcept High level categorization of audit event --></type> <subtype><!-- 0..* CodeableConcept Specific type of event --></subtype> <action value="[code]"/><!-- 0..1 Type of action performed during the event --> <severity value="[code]"/><!-- 0..1 emergency | alert | critical | error | warning | notice | informational | debug --> <occurred[x]><!-- 0..1 Period|dateTime When the activity occurred --></occurred[x]> <recorded value="[instant]"/><!-- 1..1 Time when the event was recorded --> <outcome> <!-- 0..1 Whether the event succeeded or failed --> <code><!-- 1..1 Coding Whether the event succeeded or failed --></code> <detail><!-- 0..* CodeableConcept Additional outcome detail --></detail> </outcome> <authorization><!-- 0..* CodeableConcept Authorization related to the event
--></authorization> <basedOn><!-- 0..* Reference(Any) Workflow authorization within which this event occurred --></basedOn> <patient><!-- 0..1 Reference(Patient) The patient is the subject of the data used/created/updated/deleted during the activity --></patient> <encounter><!-- 0..1 Reference(Encounter) Encounter within which this event occurred or which the event is tightly associated --></encounter> <agent> <!-- 1..* Actor involved in the event --> <type><!-- 0..1 CodeableConcept How agent participated --></type> <role><!-- 0..* CodeableConcept Agent role in the event --></role> <who><!-- 1..1 Reference(CareTeam|Device|DeviceDefinition|Group| HealthcareService|Organization|Patient|Practitioner|PractitionerRole| RelatedPerson) Identifier of who --></who> <requestor value="[boolean]"/><!-- 0..1 Whether user is initiator --> <location><!-- 0..1 Reference(Location) The agent location when the event occurred --></location> <policy value="[uri]"/><!-- 0..* Policy that authorized the agent participation in the event --> <network[x]><!-- 0..1 Reference(Endpoint)|uri|string This agent network location for the activity --></network[x]> <authorization><!-- 0..* CodeableConcept Allowable authorization for this agent
--></authorization> </agent> <source> <!-- 1..1 Audit Event Reporter --> <site><!-- 0..1 Reference(Location) Logical source location within the enterprise --></site> <observer><!-- 1..1 Reference(CareTeam|Device|Organization|Patient|Practitioner| PractitionerRole|RelatedPerson) The identity of source detecting the event --></observer> <type><!-- 0..* CodeableConcept The type of source where event originated --></type> </source> <entity> <!-- 0..* Data or objects used --> <what><!-- 0..1 Reference(Any) Specific instance of resource --></what> <role><!-- 0..1 CodeableConcept What role the entity played --></role> <securityLabel><!-- 0..* CodeableConcept Security labels on the entity --></securityLabel> <description value="[string]"/><!-- 0..1 Descriptive text --> <query value="[base64Binary]"/><!-- 0..1 Query parameters --> <detail> <!-- 0..* Additional Information about the entity --> <type><!-- 1..1 CodeableConcept The name of the extra detail property --></type> <value[x]><!-- 1..1 Quantity|CodeableConcept|string|boolean|integer|Range| Ratio|time|dateTime|Period|base64Binary Property value --></value[x]> </detail> <agent><!-- 0..* Content as for AuditEvent.agent Entity is attributed to this agent --></agent> </entity> </AuditEvent>
JSON Template
{ "resourceType" : "AuditEvent",
// from Resource: id, meta, implicitRules, and language
// from DomainResource: text, contained, extension, and modifierExtension
"type" : { CodeableConcept }, // R! High level categorization of audit event
"subtype" : [{ CodeableConcept }], // Specific type of event
"action" : "<code>", // Type of action performed during the event
"severity" : "<code>", // emergency | alert | critical | error | warning | notice | informational | debug
// occurred[x]: When the activity occurred. One of these 2:
"occurredPeriod" : { Period },
"occurredDateTime" : "<dateTime>",
"recorded" : "<instant>", // R! Time when the event was recorded
"outcome" : { // Whether the event succeeded or failed
"code" : { Coding }, // R! Whether the event succeeded or failed
"detail" : [{ CodeableConcept }] // Additional outcome detail
},
"authorization" : [{ CodeableConcept }], // Authorization related to the event
"resourceType" : "AuditEvent",
// from Resource: id, meta, implicitRules, and language
// from DomainResource: text, contained, extension, and modifierExtension
"type" : { CodeableConcept }, // R! High level categorization of audit event
"subtype" : [{ CodeableConcept }], // Specific type of event
"action" : "<code>", // Type of action performed during the event
"severity" : "<code>", // emergency | alert | critical | error | warning | notice | informational | debug
// occurred[x]: When the activity occurred. One of these 2:
"occurredPeriod" : { Period },
"occurredDateTime" : "<dateTime>",
"recorded" : "<instant>", // R! Time when the event was recorded
"outcome" : { // Whether the event succeeded or failed
"code" : { Coding }, // R! Whether the event succeeded or failed
"detail" : [{ CodeableConcept }] // Additional outcome detail
},
"authorization" : [{ CodeableConcept }], // Authorization related to the event  "basedOn" : [{ Reference(Any) }], // Workflow authorization within which this event occurred
"patient" : { Reference(Patient) }, // The patient is the subject of the data used/created/updated/deleted during the activity
"encounter" : { Reference(Encounter) }, // Encounter within which this event occurred or which the event is tightly associated
"agent" : [{ // R! Actor involved in the event
"type" : { CodeableConcept }, // How agent participated
"role" : [{ CodeableConcept }], // Agent role in the event
"who" : { Reference(CareTeam|Device|DeviceDefinition|Group|
HealthcareService|Organization|Patient|Practitioner|PractitionerRole|
RelatedPerson) }, // R! Identifier of who
"requestor" : <boolean>, // Whether user is initiator
"location" : { Reference(Location) }, // The agent location when the event occurred
"policy" : ["<uri>"], // Policy that authorized the agent participation in the event
// network[x]: This agent network location for the activity. One of these 3:
"networkReference" : { Reference(Endpoint) },
"networkUri" : "<uri>",
"networkString" : "<string>",
"authorization" : [{ CodeableConcept }] // Allowable authorization for this agent
"basedOn" : [{ Reference(Any) }], // Workflow authorization within which this event occurred
"patient" : { Reference(Patient) }, // The patient is the subject of the data used/created/updated/deleted during the activity
"encounter" : { Reference(Encounter) }, // Encounter within which this event occurred or which the event is tightly associated
"agent" : [{ // R! Actor involved in the event
"type" : { CodeableConcept }, // How agent participated
"role" : [{ CodeableConcept }], // Agent role in the event
"who" : { Reference(CareTeam|Device|DeviceDefinition|Group|
HealthcareService|Organization|Patient|Practitioner|PractitionerRole|
RelatedPerson) }, // R! Identifier of who
"requestor" : <boolean>, // Whether user is initiator
"location" : { Reference(Location) }, // The agent location when the event occurred
"policy" : ["<uri>"], // Policy that authorized the agent participation in the event
// network[x]: This agent network location for the activity. One of these 3:
"networkReference" : { Reference(Endpoint) },
"networkUri" : "<uri>",
"networkString" : "<string>",
"authorization" : [{ CodeableConcept }] // Allowable authorization for this agent  }],
"source" : { // R! Audit Event Reporter
"site" : { Reference(Location) }, // Logical source location within the enterprise
"observer" : { Reference(CareTeam|Device|Organization|Patient|Practitioner|
PractitionerRole|RelatedPerson) }, // R! The identity of source detecting the event
"type" : [{ CodeableConcept }] // The type of source where event originated
},
"entity" : [{ // Data or objects used
"what" : { Reference(Any) }, // Specific instance of resource
"role" : { CodeableConcept }, // What role the entity played
"securityLabel" : [{ CodeableConcept }], // Security labels on the entity
"description" : "<string>", // Descriptive text
"query" : "<base64Binary>", // Query parameters
"detail" : [{ // Additional Information about the entity
"type" : { CodeableConcept }, // R! The name of the extra detail property
// value[x]: Property value. One of these 11:
"valueQuantity" : { Quantity },
"valueCodeableConcept" : { CodeableConcept },
"valueString" : "<string>",
"valueBoolean" : <boolean>,
"valueInteger" : <integer>,
"valueRange" : { Range },
"valueRatio" : { Ratio },
"valueTime" : "<time>",
"valueDateTime" : "<dateTime>",
"valuePeriod" : { Period },
"valueBase64Binary" : "<base64Binary>"
}],
"agent" : [{ Content as for AuditEvent.agent }] // Entity is attributed to this agent
}]
}
}],
"source" : { // R! Audit Event Reporter
"site" : { Reference(Location) }, // Logical source location within the enterprise
"observer" : { Reference(CareTeam|Device|Organization|Patient|Practitioner|
PractitionerRole|RelatedPerson) }, // R! The identity of source detecting the event
"type" : [{ CodeableConcept }] // The type of source where event originated
},
"entity" : [{ // Data or objects used
"what" : { Reference(Any) }, // Specific instance of resource
"role" : { CodeableConcept }, // What role the entity played
"securityLabel" : [{ CodeableConcept }], // Security labels on the entity
"description" : "<string>", // Descriptive text
"query" : "<base64Binary>", // Query parameters
"detail" : [{ // Additional Information about the entity
"type" : { CodeableConcept }, // R! The name of the extra detail property
// value[x]: Property value. One of these 11:
"valueQuantity" : { Quantity },
"valueCodeableConcept" : { CodeableConcept },
"valueString" : "<string>",
"valueBoolean" : <boolean>,
"valueInteger" : <integer>,
"valueRange" : { Range },
"valueRatio" : { Ratio },
"valueTime" : "<time>",
"valueDateTime" : "<dateTime>",
"valuePeriod" : { Period },
"valueBase64Binary" : "<base64Binary>"
}],
"agent" : [{ Content as for AuditEvent.agent }] // Entity is attributed to this agent
}]
}
Turtle Template
@prefix fhir: <http://hl7.org/fhir/> .[ a fhir:AuditEvent; fhir:nodeRole fhir:treeRoot; # if this is the parser root # from Resource: fhir:id, fhir:meta, fhir:implicitRules, and fhir:language # from DomainResource: fhir:text, fhir:contained, fhir:extension, and fhir:modifierExtension fhir:type [ CodeableConcept ] ; # 1..1 High level categorization of audit event fhir:subtype ( [ CodeableConcept ] ... ) ; # 0..* Specific type of event fhir:action [ code ] ; # 0..1 Type of action performed during the event fhir:severity [ code ] ; # 0..1 emergency | alert | critical | error | warning | notice | informational | debug # occurred[x] : 0..1 When the activity occurred. One of these 2 fhir:occurred [ a fhir:Period ; Period ] fhir:occurred [ a fhir:DateTime ; dateTime ] fhir:recorded [ instant ] ; # 1..1 Time when the event was recorded fhir:outcome [ # 0..1 Whether the event succeeded or failed fhir:code [ Coding ] ; # 1..1 Whether the event succeeded or failed fhir:detail ( [ CodeableConcept ] ... ) ; # 0..* Additional outcome detail ] ; fhir:authorization ( [ CodeableConcept ] ... ) ; # 0..* Authorization related to the event fhir:basedOn ( [ Reference(Any) ] ... ) ; # 0..* Workflow authorization within which this event occurred fhir:patient [ Reference(Patient) ] ; # 0..1 The patient is the subject of the data used/created/updated/deleted during the activity fhir:encounter [ Reference(Encounter) ] ; # 0..1 Encounter within which this event occurred or which the event is tightly associated fhir:agent ( [ # 1..* Actor involved in the event fhir:type [ CodeableConcept ] ; # 0..1 How agent participated fhir:role ( [ CodeableConcept ] ... ) ; # 0..* Agent role in the event fhir:who [ Reference(CareTeam|Device|DeviceDefinition|Group|HealthcareService|Organization|Patient| Practitioner|PractitionerRole|RelatedPerson) ] ; # 1..1 Identifier of who fhir:requestor [ boolean ] ; # 0..1 Whether user is initiator fhir:location [ Reference(Location) ] ; # 0..1 The agent location when the event occurred fhir:policy ( [ uri ] ... ) ; # 0..* Policy that authorized the agent participation in the event # network[x] : 0..1 This agent network location for the activity. One of these 3 fhir:network [ a fhir:Reference ; Reference(Endpoint) ] fhir:network [ a fhir:Uri ; uri ] fhir:network [ a fhir:String ; string ] fhir:authorization ( [ CodeableConcept ] ... ) ; # 0..* Allowable authorization for this agent ] ... ) ; fhir:source [ # 1..1 Audit Event Reporter fhir:site [ Reference(Location) ] ; # 0..1 Logical source location within the enterprise fhir:observer [ Reference(CareTeam|Device|Organization|Patient|Practitioner|PractitionerRole|RelatedPerson) ] ; # 1..1 The identity of source detecting the event fhir:type ( [ CodeableConcept ] ... ) ; # 0..* The type of source where event originated ] ; fhir:entity ( [ # 0..* Data or objects used fhir:what [ Reference(Any) ] ; # 0..1 Specific instance of resource fhir:role [ CodeableConcept ] ; # 0..1 What role the entity played fhir:securityLabel ( [ CodeableConcept ] ... ) ; # 0..* Security labels on the entity fhir:description [ string ] ; # 0..1 Descriptive text fhir:query [ base64Binary ] ; # 0..1 Query parameters fhir:detail ( [ # 0..* Additional Information about the entity fhir:type [ CodeableConcept ] ; # 1..1 The name of the extra detail property # value[x] : 1..1 Property value. One of these 11 fhir:value [ a fhir:Quantity ; Quantity ] fhir:value [ a fhir:CodeableConcept ; CodeableConcept ] fhir:value [ a fhir:String ; string ] fhir:value [ a fhir:Boolean ; boolean ] fhir:value [ a fhir:Integer ; integer ] fhir:value [ a fhir:Range ; Range ] fhir:value [ a fhir:Ratio ; Ratio ] fhir:value [ a fhir:Time ; time ] fhir:value [ a fhir:DateTime ; dateTime ] fhir:value [ a fhir:Period ; Period ] fhir:value [ a fhir:Base64Binary ; base64Binary ] ] ... ) ; fhir:agent ( [ See AuditEvent.agent ] ... ) ; # 0..* Entity is attributed to this agent ] ... ) ; ]
Changes from R5 to R6
| AuditEvent | |
| AuditEvent.type |
|
| AuditEvent.subtype |
|
| AuditEvent.basedOn |
|
| AuditEvent.agent.who |
|
| AuditEvent.entity.description |
|
Changes from R4B to R6
| AuditEvent | |
| AuditEvent.type |
|
| AuditEvent.subtype |
|
| AuditEvent.severity |
|
| AuditEvent.occurred[x] |
|
| AuditEvent.outcome |
|
| AuditEvent.outcome.code |
|
| AuditEvent.outcome.detail |
|
| AuditEvent.authorization |
|
| AuditEvent.basedOn |
|
| AuditEvent.patient |
|
| AuditEvent.encounter |
|
| AuditEvent.agent.type |
|
| AuditEvent.agent.who |
|
| AuditEvent.agent.requestor |
|
| AuditEvent.agent.network[x] |
|
| AuditEvent.agent.authorization |
|
| AuditEvent.source.site |
|
| AuditEvent.source.observer |
|
| AuditEvent.source.type |
|
| AuditEvent.entity.role |
|
| AuditEvent.entity.securityLabel |
|
| AuditEvent.entity.detail.type |
|
| AuditEvent.entity.detail.value[x] |
|
| AuditEvent.entity.agent |
|
| AuditEvent.outcomeDesc |
|
| AuditEvent.agent.altId |
|
| AuditEvent.agent.name |
|
| AuditEvent.agent.media |
|
| AuditEvent.agent.network.address |
|
| AuditEvent.agent.network.type |
|
| AuditEvent.entity.type |
|
| AuditEvent.entity.lifecycle |
|
| AuditEvent.entity.name |
|
Changes from R4 to R6
| AuditEvent | |
| AuditEvent.type |
|
| AuditEvent.subtype |
|
| AuditEvent.severity |
|
| AuditEvent.occurred[x] |
|
| AuditEvent.outcome |
|
| AuditEvent.outcome.code |
|
| AuditEvent.outcome.detail |
|
| AuditEvent.authorization |
|
| AuditEvent.basedOn |
|
| AuditEvent.patient |
|
| AuditEvent.encounter |
|
| AuditEvent.agent.type |
|
| AuditEvent.agent.who |
|
| AuditEvent.agent.requestor |
|
| AuditEvent.agent.network[x] |
|
| AuditEvent.agent.authorization |
|
| AuditEvent.source.site |
|
| AuditEvent.source.observer |
|
| AuditEvent.source.type |
|
| AuditEvent.entity.role |
|
| AuditEvent.entity.securityLabel |
|
| AuditEvent.entity.detail.type |
|
| AuditEvent.entity.detail.value[x] |
|
| AuditEvent.entity.agent |
|
| AuditEvent.outcomeDesc |
|
| AuditEvent.agent.altId |
|
| AuditEvent.agent.name |
|
| AuditEvent.agent.media |
|
| AuditEvent.agent.network.address |
|
| AuditEvent.agent.network.type |
|
| AuditEvent.entity.type |
|
| AuditEvent.entity.lifecycle |
|
| AuditEvent.entity.name |
|
See the Full Difference for further information
This analysis is available for R4 as XML or JSON and for R4B as XML or JSON.
Structure
| Name | Flags | Card. | Type | Description & Constraints Filter:   |
|---|---|---|---|---|
 |
N | DomainResource | Record of an event Elements defined in Ancestors: id, meta, implicitRules, language, text, contained, extension, modifierExtension | |
  |
Σ | 1..1 | CodeableConcept | High level categorization of audit event Binding: Example Audit Event ID (Example) |
  |
Σ | 0..* | CodeableConcept | Specific type of event Binding: Example Audit Event Sub-Type (Example) |
  |
Σ | 0..1 | code | Type of action performed during the event Binding: Audit Event Action (Required) |
  |
Σ | 0..1 | code | emergency | alert | critical | error | warning | notice | informational | debug Binding: Audit Event Severity (Required) |
  |
0..1 | When the activity occurred | ||
   |
Period | |||
   |
dateTime | |||
  |
Σ | 1..1 | instant | Time when the event was recorded |
  |
Σ | 0..1 | BackboneElement | Whether the event succeeded or failed |
   |
Σ | 1..1 | Coding | Whether the event succeeded or failed Binding: Example Audit Event Outcome (Preferred) |
   |
Σ | 0..* | CodeableConcept | Additional outcome detail Binding: Example Audit Event Outcome Detail (Example) |
  |
Σ | 0..* | CodeableConcept | Authorization related to the event Binding: PurposeOfUse  (Example) (Example) |
  |
0..* | Reference(Any) | Workflow authorization within which this event occurred | |
  |
Σ | 0..1 | Reference(Patient) | The patient is the subject of the data used/created/updated/deleted during the activity |
  |
0..1 | Reference(Encounter) | Encounter within which this event occurred or which the event is tightly associated | |
  |
Σ | 1..* | BackboneElement | Actor involved in the event |
   |
0..1 | CodeableConcept | How agent participated Binding: Participation Role Type (Preferred) | |
   |
0..* | CodeableConcept | Agent role in the event Binding: Example Security Role Type (Example) | |
   |
Σ | 1..1 | Reference(Practitioner | PractitionerRole | Organization | CareTeam | Patient | Device | DeviceDefinition | RelatedPerson | Group | HealthcareService) | Identifier of who |
   |
Σ | 0..1 | boolean | Whether user is initiator |
   |
0..1 | Reference(Location) | The agent location when the event occurred | |
   |
0..* | uri | Policy that authorized the agent participation in the event | |
   |
0..1 | This agent network location for the activity | ||
    |
Reference(Endpoint) | |||
    |
uri | |||
    |
string | |||
   |
0..* | CodeableConcept | Allowable authorization for this agent Binding: PurposeOfUse  (Example) (Example) | |
  |
Σ | 1..1 | BackboneElement | Audit Event Reporter |
   |
0..1 | Reference(Location) | Logical source location within the enterprise | |
   |
Σ | 1..1 | Reference(Practitioner | PractitionerRole | Organization | CareTeam | Patient | Device | RelatedPerson) | The identity of source detecting the event |
   |
0..* | CodeableConcept | The type of source where event originated Binding: Audit Event Source Type (Preferred) | |
  |
Σ | 0..* | BackboneElement | Data or objects used |
   |
Σ | 0..1 | Reference(Any) | Specific instance of resource |
   |
0..1 | CodeableConcept | What role the entity played Binding: Example Audit Event Entity Role (Example) | |
   |
0..* | CodeableConcept | Security labels on the entity Binding: Example set of Security Labels (Example) | |
   |
0..1 | string | Descriptive text | |
   |
Σ | 0..1 | base64Binary | Query parameters |
   |
0..* | BackboneElement | Additional Information about the entity | |
    |
1..1 | CodeableConcept | The name of the extra detail property Binding: Example value set Audit Event Entity Detail Type (Example) | |
    |
1..1 | Property value | ||
     |
Quantity | |||
     |
CodeableConcept | |||
     |
string | |||
     |
boolean | |||
     |
integer | |||
     |
Range | |||
     |
Ratio | |||
     |
time | |||
     |
dateTime | |||
     |
Period | |||
     |
base64Binary | |||
   |
0..* | see agent | Entity is attributed to this agent | |
 Documentation for this format Documentation for this format  | ||||
See the Extensions for this resource
XML Template
<AuditEvent xmlns="http://hl7.org/fhir"><!-- from Resource: id, meta, implicitRules, and language --> <!-- from DomainResource: text, contained, extension, and modifierExtension --> <type><!-- 1..1 CodeableConcept High level categorization of audit event --></type> <subtype><!-- 0..* CodeableConcept Specific type of event --></subtype> <action value="[code]"/><!-- 0..1 Type of action performed during the event --> <severity value="[code]"/><!-- 0..1 emergency | alert | critical | error | warning | notice | informational | debug --> <occurred[x]><!-- 0..1 Period|dateTime When the activity occurred --></occurred[x]> <recorded value="[instant]"/><!-- 1..1 Time when the event was recorded --> <outcome> <!-- 0..1 Whether the event succeeded or failed --> <code><!-- 1..1 Coding Whether the event succeeded or failed --></code> <detail><!-- 0..* CodeableConcept Additional outcome detail --></detail> </outcome> <authorization><!-- 0..* CodeableConcept Authorization related to the event
--></authorization> <basedOn><!-- 0..* Reference(Any) Workflow authorization within which this event occurred --></basedOn> <patient><!-- 0..1 Reference(Patient) The patient is the subject of the data used/created/updated/deleted during the activity --></patient> <encounter><!-- 0..1 Reference(Encounter) Encounter within which this event occurred or which the event is tightly associated --></encounter> <agent> <!-- 1..* Actor involved in the event --> <type><!-- 0..1 CodeableConcept How agent participated --></type> <role><!-- 0..* CodeableConcept Agent role in the event --></role> <who><!-- 1..1 Reference(CareTeam|Device|DeviceDefinition|Group| HealthcareService|Organization|Patient|Practitioner|PractitionerRole| RelatedPerson) Identifier of who --></who> <requestor value="[boolean]"/><!-- 0..1 Whether user is initiator --> <location><!-- 0..1 Reference(Location) The agent location when the event occurred --></location> <policy value="[uri]"/><!-- 0..* Policy that authorized the agent participation in the event --> <network[x]><!-- 0..1 Reference(Endpoint)|uri|string This agent network location for the activity --></network[x]> <authorization><!-- 0..* CodeableConcept Allowable authorization for this agent
--></authorization> </agent> <source> <!-- 1..1 Audit Event Reporter --> <site><!-- 0..1 Reference(Location) Logical source location within the enterprise --></site> <observer><!-- 1..1 Reference(CareTeam|Device|Organization|Patient|Practitioner| PractitionerRole|RelatedPerson) The identity of source detecting the event --></observer> <type><!-- 0..* CodeableConcept The type of source where event originated --></type> </source> <entity> <!-- 0..* Data or objects used --> <what><!-- 0..1 Reference(Any) Specific instance of resource --></what> <role><!-- 0..1 CodeableConcept What role the entity played --></role> <securityLabel><!-- 0..* CodeableConcept Security labels on the entity --></securityLabel> <description value="[string]"/><!-- 0..1 Descriptive text --> <query value="[base64Binary]"/><!-- 0..1 Query parameters --> <detail> <!-- 0..* Additional Information about the entity --> <type><!-- 1..1 CodeableConcept The name of the extra detail property --></type> <value[x]><!-- 1..1 Quantity|CodeableConcept|string|boolean|integer|Range| Ratio|time|dateTime|Period|base64Binary Property value --></value[x]> </detail> <agent><!-- 0..* Content as for AuditEvent.agent Entity is attributed to this agent --></agent> </entity> </AuditEvent>
JSON Template
{ "resourceType" : "AuditEvent",
// from Resource: id, meta, implicitRules, and language
// from DomainResource: text, contained, extension, and modifierExtension
"type" : { CodeableConcept }, // R! High level categorization of audit event
"subtype" : [{ CodeableConcept }], // Specific type of event
"action" : "<code>", // Type of action performed during the event
"severity" : "<code>", // emergency | alert | critical | error | warning | notice | informational | debug
// occurred[x]: When the activity occurred. One of these 2:
"occurredPeriod" : { Period },
"occurredDateTime" : "<dateTime>",
"recorded" : "<instant>", // R! Time when the event was recorded
"outcome" : { // Whether the event succeeded or failed
"code" : { Coding }, // R! Whether the event succeeded or failed
"detail" : [{ CodeableConcept }] // Additional outcome detail
},
"authorization" : [{ CodeableConcept }], // Authorization related to the event
"resourceType" : "AuditEvent",
// from Resource: id, meta, implicitRules, and language
// from DomainResource: text, contained, extension, and modifierExtension
"type" : { CodeableConcept }, // R! High level categorization of audit event
"subtype" : [{ CodeableConcept }], // Specific type of event
"action" : "<code>", // Type of action performed during the event
"severity" : "<code>", // emergency | alert | critical | error | warning | notice | informational | debug
// occurred[x]: When the activity occurred. One of these 2:
"occurredPeriod" : { Period },
"occurredDateTime" : "<dateTime>",
"recorded" : "<instant>", // R! Time when the event was recorded
"outcome" : { // Whether the event succeeded or failed
"code" : { Coding }, // R! Whether the event succeeded or failed
"detail" : [{ CodeableConcept }] // Additional outcome detail
},
"authorization" : [{ CodeableConcept }], // Authorization related to the event  "basedOn" : [{ Reference(Any) }], // Workflow authorization within which this event occurred
"patient" : { Reference(Patient) }, // The patient is the subject of the data used/created/updated/deleted during the activity
"encounter" : { Reference(Encounter) }, // Encounter within which this event occurred or which the event is tightly associated
"agent" : [{ // R! Actor involved in the event
"type" : { CodeableConcept }, // How agent participated
"role" : [{ CodeableConcept }], // Agent role in the event
"who" : { Reference(CareTeam|Device|DeviceDefinition|Group|
HealthcareService|Organization|Patient|Practitioner|PractitionerRole|
RelatedPerson) }, // R! Identifier of who
"requestor" : <boolean>, // Whether user is initiator
"location" : { Reference(Location) }, // The agent location when the event occurred
"policy" : ["<uri>"], // Policy that authorized the agent participation in the event
// network[x]: This agent network location for the activity. One of these 3:
"networkReference" : { Reference(Endpoint) },
"networkUri" : "<uri>",
"networkString" : "<string>",
"authorization" : [{ CodeableConcept }] // Allowable authorization for this agent
"basedOn" : [{ Reference(Any) }], // Workflow authorization within which this event occurred
"patient" : { Reference(Patient) }, // The patient is the subject of the data used/created/updated/deleted during the activity
"encounter" : { Reference(Encounter) }, // Encounter within which this event occurred or which the event is tightly associated
"agent" : [{ // R! Actor involved in the event
"type" : { CodeableConcept }, // How agent participated
"role" : [{ CodeableConcept }], // Agent role in the event
"who" : { Reference(CareTeam|Device|DeviceDefinition|Group|
HealthcareService|Organization|Patient|Practitioner|PractitionerRole|
RelatedPerson) }, // R! Identifier of who
"requestor" : <boolean>, // Whether user is initiator
"location" : { Reference(Location) }, // The agent location when the event occurred
"policy" : ["<uri>"], // Policy that authorized the agent participation in the event
// network[x]: This agent network location for the activity. One of these 3:
"networkReference" : { Reference(Endpoint) },
"networkUri" : "<uri>",
"networkString" : "<string>",
"authorization" : [{ CodeableConcept }] // Allowable authorization for this agent  }],
"source" : { // R! Audit Event Reporter
"site" : { Reference(Location) }, // Logical source location within the enterprise
"observer" : { Reference(CareTeam|Device|Organization|Patient|Practitioner|
PractitionerRole|RelatedPerson) }, // R! The identity of source detecting the event
"type" : [{ CodeableConcept }] // The type of source where event originated
},
"entity" : [{ // Data or objects used
"what" : { Reference(Any) }, // Specific instance of resource
"role" : { CodeableConcept }, // What role the entity played
"securityLabel" : [{ CodeableConcept }], // Security labels on the entity
"description" : "<string>", // Descriptive text
"query" : "<base64Binary>", // Query parameters
"detail" : [{ // Additional Information about the entity
"type" : { CodeableConcept }, // R! The name of the extra detail property
// value[x]: Property value. One of these 11:
"valueQuantity" : { Quantity },
"valueCodeableConcept" : { CodeableConcept },
"valueString" : "<string>",
"valueBoolean" : <boolean>,
"valueInteger" : <integer>,
"valueRange" : { Range },
"valueRatio" : { Ratio },
"valueTime" : "<time>",
"valueDateTime" : "<dateTime>",
"valuePeriod" : { Period },
"valueBase64Binary" : "<base64Binary>"
}],
"agent" : [{ Content as for AuditEvent.agent }] // Entity is attributed to this agent
}]
}
}],
"source" : { // R! Audit Event Reporter
"site" : { Reference(Location) }, // Logical source location within the enterprise
"observer" : { Reference(CareTeam|Device|Organization|Patient|Practitioner|
PractitionerRole|RelatedPerson) }, // R! The identity of source detecting the event
"type" : [{ CodeableConcept }] // The type of source where event originated
},
"entity" : [{ // Data or objects used
"what" : { Reference(Any) }, // Specific instance of resource
"role" : { CodeableConcept }, // What role the entity played
"securityLabel" : [{ CodeableConcept }], // Security labels on the entity
"description" : "<string>", // Descriptive text
"query" : "<base64Binary>", // Query parameters
"detail" : [{ // Additional Information about the entity
"type" : { CodeableConcept }, // R! The name of the extra detail property
// value[x]: Property value. One of these 11:
"valueQuantity" : { Quantity },
"valueCodeableConcept" : { CodeableConcept },
"valueString" : "<string>",
"valueBoolean" : <boolean>,
"valueInteger" : <integer>,
"valueRange" : { Range },
"valueRatio" : { Ratio },
"valueTime" : "<time>",
"valueDateTime" : "<dateTime>",
"valuePeriod" : { Period },
"valueBase64Binary" : "<base64Binary>"
}],
"agent" : [{ Content as for AuditEvent.agent }] // Entity is attributed to this agent
}]
}
Turtle Template
@prefix fhir: <http://hl7.org/fhir/> .[ a fhir:AuditEvent; fhir:nodeRole fhir:treeRoot; # if this is the parser root # from Resource: fhir:id, fhir:meta, fhir:implicitRules, and fhir:language # from DomainResource: fhir:text, fhir:contained, fhir:extension, and fhir:modifierExtension fhir:type [ CodeableConcept ] ; # 1..1 High level categorization of audit event fhir:subtype ( [ CodeableConcept ] ... ) ; # 0..* Specific type of event fhir:action [ code ] ; # 0..1 Type of action performed during the event fhir:severity [ code ] ; # 0..1 emergency | alert | critical | error | warning | notice | informational | debug # occurred[x] : 0..1 When the activity occurred. One of these 2 fhir:occurred [ a fhir:Period ; Period ] fhir:occurred [ a fhir:DateTime ; dateTime ] fhir:recorded [ instant ] ; # 1..1 Time when the event was recorded fhir:outcome [ # 0..1 Whether the event succeeded or failed fhir:code [ Coding ] ; # 1..1 Whether the event succeeded or failed fhir:detail ( [ CodeableConcept ] ... ) ; # 0..* Additional outcome detail ] ; fhir:authorization ( [ CodeableConcept ] ... ) ; # 0..* Authorization related to the event fhir:basedOn ( [ Reference(Any) ] ... ) ; # 0..* Workflow authorization within which this event occurred fhir:patient [ Reference(Patient) ] ; # 0..1 The patient is the subject of the data used/created/updated/deleted during the activity fhir:encounter [ Reference(Encounter) ] ; # 0..1 Encounter within which this event occurred or which the event is tightly associated fhir:agent ( [ # 1..* Actor involved in the event fhir:type [ CodeableConcept ] ; # 0..1 How agent participated fhir:role ( [ CodeableConcept ] ... ) ; # 0..* Agent role in the event fhir:who [ Reference(CareTeam|Device|DeviceDefinition|Group|HealthcareService|Organization|Patient| Practitioner|PractitionerRole|RelatedPerson) ] ; # 1..1 Identifier of who fhir:requestor [ boolean ] ; # 0..1 Whether user is initiator fhir:location [ Reference(Location) ] ; # 0..1 The agent location when the event occurred fhir:policy ( [ uri ] ... ) ; # 0..* Policy that authorized the agent participation in the event # network[x] : 0..1 This agent network location for the activity. One of these 3 fhir:network [ a fhir:Reference ; Reference(Endpoint) ] fhir:network [ a fhir:Uri ; uri ] fhir:network [ a fhir:String ; string ] fhir:authorization ( [ CodeableConcept ] ... ) ; # 0..* Allowable authorization for this agent ] ... ) ; fhir:source [ # 1..1 Audit Event Reporter fhir:site [ Reference(Location) ] ; # 0..1 Logical source location within the enterprise fhir:observer [ Reference(CareTeam|Device|Organization|Patient|Practitioner|PractitionerRole|RelatedPerson) ] ; # 1..1 The identity of source detecting the event fhir:type ( [ CodeableConcept ] ... ) ; # 0..* The type of source where event originated ] ; fhir:entity ( [ # 0..* Data or objects used fhir:what [ Reference(Any) ] ; # 0..1 Specific instance of resource fhir:role [ CodeableConcept ] ; # 0..1 What role the entity played fhir:securityLabel ( [ CodeableConcept ] ... ) ; # 0..* Security labels on the entity fhir:description [ string ] ; # 0..1 Descriptive text fhir:query [ base64Binary ] ; # 0..1 Query parameters fhir:detail ( [ # 0..* Additional Information about the entity fhir:type [ CodeableConcept ] ; # 1..1 The name of the extra detail property # value[x] : 1..1 Property value. One of these 11 fhir:value [ a fhir:Quantity ; Quantity ] fhir:value [ a fhir:CodeableConcept ; CodeableConcept ] fhir:value [ a fhir:String ; string ] fhir:value [ a fhir:Boolean ; boolean ] fhir:value [ a fhir:Integer ; integer ] fhir:value [ a fhir:Range ; Range ] fhir:value [ a fhir:Ratio ; Ratio ] fhir:value [ a fhir:Time ; time ] fhir:value [ a fhir:DateTime ; dateTime ] fhir:value [ a fhir:Period ; Period ] fhir:value [ a fhir:Base64Binary ; base64Binary ] ] ... ) ; fhir:agent ( [ See AuditEvent.agent ] ... ) ; # 0..* Entity is attributed to this agent ] ... ) ; ]
Changes from R5 to R6
| AuditEvent | |
| AuditEvent.type |
|
| AuditEvent.subtype |
|
| AuditEvent.basedOn |
|
| AuditEvent.agent.who |
|
| AuditEvent.entity.description |
|
Changes from R4B to R6
| AuditEvent | |
| AuditEvent.type |
|
| AuditEvent.subtype |
|
| AuditEvent.severity |
|
| AuditEvent.occurred[x] |
|
| AuditEvent.outcome |
|
| AuditEvent.outcome.code |
|
| AuditEvent.outcome.detail |
|
| AuditEvent.authorization |
|
| AuditEvent.basedOn |
|
| AuditEvent.patient |
|
| AuditEvent.encounter |
|
| AuditEvent.agent.type |
|
| AuditEvent.agent.who |
|
| AuditEvent.agent.requestor |
|
| AuditEvent.agent.network[x] |
|
| AuditEvent.agent.authorization |
|
| AuditEvent.source.site |
|
| AuditEvent.source.observer |
|
| AuditEvent.source.type |
|
| AuditEvent.entity.role |
|
| AuditEvent.entity.securityLabel |
|
| AuditEvent.entity.detail.type |
|
| AuditEvent.entity.detail.value[x] |
|
| AuditEvent.entity.agent |
|
| AuditEvent.outcomeDesc |
|
| AuditEvent.agent.altId |
|
| AuditEvent.agent.name |
|
| AuditEvent.agent.media |
|
| AuditEvent.agent.network.address |
|
| AuditEvent.agent.network.type |
|
| AuditEvent.entity.type |
|
| AuditEvent.entity.lifecycle |
|
| AuditEvent.entity.name |
|
Changes from R4 to R6
| AuditEvent | |
| AuditEvent.type |
|
| AuditEvent.subtype |
|
| AuditEvent.severity |
|
| AuditEvent.occurred[x] |
|
| AuditEvent.outcome |
|
| AuditEvent.outcome.code |
|
| AuditEvent.outcome.detail |
|
| AuditEvent.authorization |
|
| AuditEvent.basedOn |
|
| AuditEvent.patient |
|
| AuditEvent.encounter |
|
| AuditEvent.agent.type |
|
| AuditEvent.agent.who |
|
| AuditEvent.agent.requestor |
|
| AuditEvent.agent.network[x] |
|
| AuditEvent.agent.authorization |
|
| AuditEvent.source.site |
|
| AuditEvent.source.observer |
|
| AuditEvent.source.type |
|
| AuditEvent.entity.role |
|
| AuditEvent.entity.securityLabel |
|
| AuditEvent.entity.detail.type |
|
| AuditEvent.entity.detail.value[x] |
|
| AuditEvent.entity.agent |
|
| AuditEvent.outcomeDesc |
|
| AuditEvent.agent.altId |
|
| AuditEvent.agent.name |
|
| AuditEvent.agent.media |
|
| AuditEvent.agent.network.address |
|
| AuditEvent.agent.network.type |
|
| AuditEvent.entity.type |
|
| AuditEvent.entity.lifecycle |
|
| AuditEvent.entity.name |
|
See the Full Difference for further information
This analysis is available for R4 as XML or JSON and for R4B as XML or JSON.
Additional definitions: Master Definition XML + JSON, XML Schema/Schematron + JSON Schema, ShEx (for Turtle) + see the extensions, the spreadsheet version & the dependency analysis
| Path | ValueSet | Type | Documentation |
|---|---|---|---|
| AuditEvent.type | AuditEventIDExample | Example | Example value set of Event Categories for Audit Events - defined by DICOM with some FHIR specific additions. |
| AuditEvent.subtype | AuditEventSubTypeExample | Example | Example values for more detailed code concerning the type of the audit event - defined by DICOM with some additional FHIR, HL7, and other additions. |
| AuditEvent.action | AuditEventAction | Required | Indicator value set for type of action performed during the event that generated the event. |
| AuditEvent.severity | AuditEventSeverity | Required | The severity of the audit entry. |
| AuditEvent.outcome.code | AuditEventOutcomeExample (a valid code from Issue Severity) | Preferred | Example codes to indicate whether the event succeeded or failed. |
| AuditEvent.outcome.detail | AuditEventOutcomeDetailExample (a valid code from Operation Outcome Codes  ) ) |
Example | Example values to indicate more detailed reason for outcome. |
| AuditEvent.authorization | PurposeOfUse  |
Example | Supports communication of purpose of use at a general level. |
| AuditEvent.agent.type | ParticipationRoleType | Preferred | This FHIR value set is comprised of Actor participation Type codes, which can be used to value FHIR agents, actors, and other role elements. The codes are intended to express how the agent participated in some activity. Sometimes refered to the agent functional-role relative to the activity. |
| AuditEvent.agent.role | SecurityRoleTypeExamples (a valid code from Example Codes for Security Structural Role) | Example | This value set contains example structural roles. In general, two types of roles can be distinguished: structural roles and functional roles. Structural Roles reflect human or organizational categories (hierarchies), and describe prerequisites, feasibilities, or competences for actions. Functional roles are bound to the realization or performance of actions. |
| AuditEvent.agent.authorization | PurposeOfUse  |
Example | Supports communication of purpose of use at a general level. |
| AuditEvent.source.type | AuditEventSourceType | Preferred | The type of process where the audit event originated from. Use of these codes is not required but is encouraged to maintain translation with DICOM AuditMessage schema. |
| AuditEvent.entity.role | AuditEventEntityRoleExample (a valid code from AuditEventEntityRole  ) ) |
Example | Example codes representing the role the entity played in the audit event. |
| AuditEvent.entity.securityLabel | SecurityLabelExamples | Example | A sample of security labels from Healthcare Privacy and Security Classification System as the combination of data and event codes. |
| AuditEvent.entity.detail.type | AuditEventEntityDetailTypeExamples (a valid code from Example Codes for AuditEvent.entity.detail.type) | Example | Example values for the type of additional detail about an entity used in an event. |
The AuditEvent resource and the ATNA Audit record are used in many contexts throughout healthcare. The coded values defined in the "extensible" bindings above are those widely used and/or defined by DICOM, IHE or ISO, who defined these codes to meet very specific use cases. These codes SHOULD be used when they are suitable. When needed, other codes can be defined.
Note: When using codes from a vocabulary, the display element for the code can be left off to keep the
AuditEvent size small and minimize impact of a large audit log of similar entries.
The set of codes defined for this resource is expected to grow over time, and additional codes MAY be proposed / requested using the "Propose a change" link above below.
This table summarizes common event scenarios, and the codes that SHOULD be used for each case.
| Scenario | category | code | action | Other |
| User Login (example) |
110114  User Authentication User Authentication |
110122  User Authentication User Authentication |
E Execute | One agent which contains the details of the logged-in user. |
| User Logout (example) |
110114  User Authentication User Authentication |
110123  User Logout User Logout |
E Execute | One agent which contains the details of the logged-out user. |
| REST operation logged on server (example) | rest RESTful Operation | [code] defined for operation | * (see below) | Agent for logged in user, if available. |
| Search operation logged on server (example) | rest RESTful Operation | [code] defined for operation | E Execute | Agent for logged in user, if available, and one object with a query element. The Execute action is used as the server must execute the search parameters to get the results, whereas a Read action identifies a specific object. |
| Break-Glass started (example) |
110113  Security Alert Security Alert |
110127  Emergency Override Started Emergency Override Started |
E Execute | Agent is the user who is authorized to break-glass and has declared an emergency override. Note there is an Emergency Override Stopped code that can be used to indicate the closing of the break-glass event, when it is known. |
Audit Event Actions for RESTful operations:
| Operation | Action |
| create | C |
| read, vread, history-instance, history-type, history-system | R |
| update | U |
| delete | D |
| transaction, operation, conformance, validate, search, search-type, search-system | E |
A search event is recorded as an Execute action as the server must execute the search parameters to get the results. The category is a rest operation. The code SHOULD be search. The Server is identified in an .agent as the role Destination Role ID, and the client is identified in an .agent as the role Source Role ID. Additional .agent elements MAY be used to identify user, application, organization, etc.
A Search Event records one .entity element that holds the search request, and SHOULD NOT record the contents of the search response so as to limit duplication of sensitive health information that is already present in the system, and discoverable by replaying the search request.
The AuditEvent.entity.query SHALL hold the whole WHOLE http header and body encoded as base64binary. This SHOULD preserve as much of the raw http header and body as possible to best capture any attempts by clients or intermediaries to misbehave. There SHOULD be no sanitization or normalization of this value.
The FHIR specification defines a harmonized search parameter string, which is returned in the searchset bundle as the .link.url on the .link for self. This string could be recorded in the AuditEvent.entry.description as it is well behaved and represents what was actually processed as search parameters. See: conformance 
Where there are identifiable Patient subject(s) associated with the returned Resource(s), the AuditEvent.patient SHOULD be used to record the Patient as the subject of the data or activity. When multiple patient results are returned one AuditEvent is created for every Patient identified in the resulting search set. Note this is true when the search set bundle includes any number of resources that collectively reference multiple Patients. This includes one Resource with multiple subject values, or many Resources with single subject values that are different.
FHIR interactions can result in a rich description of the outcome using the OperationOutcome. The OperationOutcome Resource is a collection of error, warning or information messages that result from a system action. This describes in detail the outcome of some operation, such as when a RESTful operation fails.
When recording into an AuditEvent that some FHIR interaction has happened, the AuditEvent SHOULD include the OperationOutcome from that FHIR interaction. This is done by placing the OperationOutcome into an AuditEvent.entity. Likely as a contained resource, given that OperationOutcome resources often are not persisted.
entity.what is the OperationOutcome -- Likely contained
entity.type is code
OperationOutcome
entity.description explains why this OperationOutcome was included.
See transaction failure example: When a client attempts to post (create) an Observation Resource,
using a server Patient endpoint;
this would result in an error with an OperationOutcome.
The AuditEvent provides the element AuditEvent.authorization to convey the purpose of use for the whole event and AuditEvent.agent.authorization
to convey the purpose of use that a particular actor (machine, person, software) was involved in the event.
AuditEvent.authorization is an element at the level of AuditEvent and can convey the purpose of the activity
that resulted in the event. This will occur when the system that is reporting the event is aware
of the purpose of the event. A specific example would be a radiology reporting system where a
radiologist has created and is sending a finished report. This system likely knows the purpose,
e.g., "treatment". It is multi-valued because the one event MAY be related to multiple purposes.
It is also commonplace that the reporting system does not have information about the purpose of the event. In these cases, the event report would not have an authorization.
It is also likely that the same event will be reported from different perspectives, e.g., by both the sender and recipient of a communication. These two different perspectives can have different knowledge regarding the purposeOfUse authorization.
AuditEvent.agent.authorization is an element at the level of agent within AuditEvent. This describes the reason that this
person, machine, or software is participating in the activity that resulted in the event. For
example, an individual person participating in the event MAY assert a purpose of use from their perspective.
It is also possible that they are participating for multiple reasons and report multiple purposeOfUse.
The reporting system might not have knowledge regarding why a particular machine or person was involved and would omit this element in those cases.
When the same event is reported from multiple perspectives, the reports can have different knowledge regarding the purpose.
It is a best practice to include a reference to the Patient affected by any auditable event, in order to enable Privacy Accounting of Disclosures and Access Logs, and to enable privacy office and security office audit log analysis. Reasonable efforts SHOULD be taken to assure the Patient is recorded, but it is recognized that there are times when this is not reasonable.
Where an activity impacts more than one Patient subject; multiple AuditEvent resources SHOULD be recorded, one for each Patient subject. This best enables segmentation of the AuditEvent details so as to limit the Privacy impact. The use of multiple AuditEvent is a best-practice and SHOULD be driven by a Policy. There will be cases where the use of multiple AuditEvent resources are not necessary, such as public health reporting.
To record a REST interaction or $operation, it is often necessary to complete the transaction in order to determine the Patient subject. Inspection of the potential returned results MAY be necessary. Some REST and $operations include parameters limiting the results to a specific Patient, in these cases this parameter informs the inclusion of the Patient reference.
Implementation Guides MAY make the AuditEvent requirements more clear given the workflow or security context mandated by the Implementation Guide.
Search parameters for this resource. See also the full list of search parameters for this resource, and check the Extensions registry for search parameters on extensions related to this resource. The common parameters also apply. See Searching for more information about searching in REST, messaging, and services.
| Name | Type | Description | Expression | In Common |
| action | token | Type of action performed during the event | AuditEvent.action | |
| agent | reference | Identifier of who | AuditEvent.agent.who (Practitioner, Group, Organization, CareTeam, Device, DeviceDefinition, Patient, HealthcareService, PractitionerRole, RelatedPerson) |
|
| agent-role | token | Agent role in the event | AuditEvent.agent.role | |
| based-on | reference | Reference to the service request. | AuditEvent.basedOn (Any) |
|
| date | date | Time when the event was recorded | AuditEvent.recorded | 22 Resources |
| encounter | reference | Encounter related to the activity recorded in the AuditEvent | AuditEvent.encounter (Encounter) |
26 Resources |
| entity | reference | Specific instance of resource | AuditEvent.entity.what (Any) |
|
| entity-desc | string | Description of an entity | AuditEvent.entity.description | |
| entity-role | token | What role the entity played | AuditEvent.entity.role | |
| outcome | token | Whether the event succeeded or failed | AuditEvent.outcome.code | |
| patient | reference | Where the activity involved patient data | AuditEvent.patient (Patient) |
60 Resources |
| policy | uri | Policy that authorized event | AuditEvent.agent.policy | |
| purpose | token | The authorization (purposeOfUse) of the event | AuditEvent.authorization | AuditEvent.agent.authorization | |
| source | reference | The identity of source detecting the event | AuditEvent.source.observer (Practitioner, Organization, CareTeam, Device, Patient, PractitionerRole, RelatedPerson) |
|
| subtype | token | More specific code for the event | AuditEvent.subtype | |
| type | token | Type (category) of event | AuditEvent.type |