|
Type
|
Reference
|
Content
|
|
web
|
example.org
|
who
: http://example.org/fhir/Patient/ex-patient
|
|
web
|
example.org
|
what
: http://example.org/fhir/Patient/ex-patient
|
|
web
|
example.org
|
what
: http://example.org/fhir/Consent/ex-consent
|
|
web
|
profiles.ihe.net
|
This Actor is derived off of the ATNA Secure Application
or ATNA Secure Node
actor
with ATNA ATX:FHIR Feed Option
.
|
|
web
|
profiles.ihe.net
|
This Actor is derived off of the ATNA Secure Application
or ATNA Secure Node
actor
with ATNA ATX:FHIR Feed Option
.
|
|
web
|
profiles.ihe.net
|
This Actor is derived off of the ATNA Secure Application
or ATNA Secure Node
actor
with ATNA ATX:FHIR Feed Option
.
|
|
web
|
profiles.ihe.net
|
ATNA
required, encouraged IHE-IUA
or SMART-on-FHIR
|
|
web
|
profiles.ihe.net
|
ATNA
required, encouraged IHE-IUA
or SMART-on-FHIR
|
|
web
|
profiles.ihe.net
|

|
|
web
|
profiles.ihe.net
|

|
|
web
|
github.com
|
De-Identification Profile, published by IHE IT Infrastructure Technical Committee. This guide is not an authorized publication; it is the continuous build for version 0.0.1-current built by the FHIR (HL7® FHIR® Standard) CI Build. This version is based on the current content of https://github.com/IHE/ITI.DeIdHandbook/
and changes regularly. See the Directory of published versions
|
|
web
|
www.ihe.net
|
IG © 2021+ IHE IT Infrastructure Technical Committee
. Package ihe.iti.deid#0.0.1-current based on FHIR 4.0.1
. Generated 2026-02-16
Links: Table of Contents |
QA Report
| New Issue | Issues
Version History |
 |
Propose a change |
Propose a change
|
|
web
|
github.com
|
Links: Table of Contents
|
QA Report
| New Issue
| Issues
Version History
|
 |
Propose a change
|
Propose a change
|
|
web
|
github.com
|
Links: Table of Contents
|
QA Report
| New Issue
| Issues
Version History
|
 |
Propose a change
|
Propose a change
|
|
web
|
profiles.ihe.net
|
Links: Table of Contents
|
QA Report
| New Issue
| Issues
Version History
|
 |
Propose a change
|
Propose a change
|
|
web
|
www.ihe.net
|
Links: Table of Contents
|
QA Report
| New Issue
| Issues
Version History
|
 |
Propose a change
|
Propose a change
|
|
web
|
profiles.ihe.net
|
This Actor is derived off of the ATNA Secure Application
or ATNA Secure Node
actor
with ATNA ATX:FHIR Feed Option
.
|
|
web
|
profiles.ihe.net
|
This Actor is derived off of the ATNA Secure Application
or ATNA Secure Node
actor
with ATNA ATX:FHIR Feed Option
.
|
|
web
|
profiles.ihe.net
|
This Actor is derived off of the ATNA Secure Application
or ATNA Secure Node
actor
with ATNA ATX:FHIR Feed Option
.
|
|
web
|
gdpr-info.eu
|
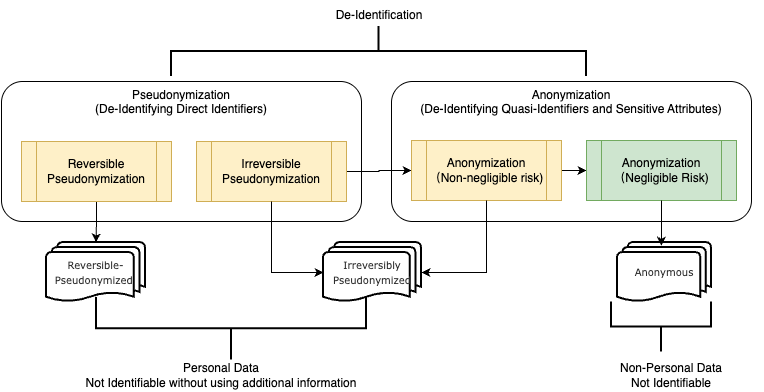
The principles of data protection should therefore not apply to anonymous information, namely information which does not relate to an identified or identifiable natural person or to personal data rendered anonymous in such a manner that the data subject is not or no longer identifiable. Recital 26, GDPR
.
|
|
web
|
en.npc.gov.cn.cdurl.cn
|
"anonymization" refers to the process of processing personal information to make it impossible to identify specific natural persons and impossible to restore. Art 73 (4), PIPL
|
|
web
|
curia.europa.eu
|
A practical anonymization is prefered. (ISO 25237, 2017)
acknowledges that an absolute definition of anonymization is difficult to achieve and often impractical, favoring a practical approach that is increasingly widely accepted. The legal practices also show a preferences of a practical anonymization. In Case C-582/14
, the Court of Justice of the European Union (CJEU) held that a dynamic IP address qualifies as personal data for a website operator only if the operator has legal means reasonably likely to access additional identifying information, such as from an internet service provider. More recently, Case T-557/20
from the CJEU provided a key precedent by delineating pseudonymized from anonymized data in cross-entity data-sharing contexts. The court introduced the "reasonable likelihood" standard, stressing that data’s status as personal hinges on the recipient’s actual re-identification capability, not theoretical potential. This pragmatic stance aligns with the Expert Determination method under the HIPAA Privacy Rule (45 C.F.R. §164.514(b)). Likewise, China is crafting data anonymization standards that adopt a practical lens, assessing re-identification risk from the recipient’s perspective. Recognizing that such risks cannot be fully eradicated, these standards prioritize governance measures alongside technical safeguards.
|
|
web
|
curia.europa.eu
|
A practical anonymization is prefered. (ISO 25237, 2017)
acknowledges that an absolute definition of anonymization is difficult to achieve and often impractical, favoring a practical approach that is increasingly widely accepted. The legal practices also show a preferences of a practical anonymization. In Case C-582/14
, the Court of Justice of the European Union (CJEU) held that a dynamic IP address qualifies as personal data for a website operator only if the operator has legal means reasonably likely to access additional identifying information, such as from an internet service provider. More recently, Case T-557/20
from the CJEU provided a key precedent by delineating pseudonymized from anonymized data in cross-entity data-sharing contexts. The court introduced the "reasonable likelihood" standard, stressing that data’s status as personal hinges on the recipient’s actual re-identification capability, not theoretical potential. This pragmatic stance aligns with the Expert Determination method under the HIPAA Privacy Rule (45 C.F.R. §164.514(b)). Likewise, China is crafting data anonymization standards that adopt a practical lens, assessing re-identification risk from the recipient’s perspective. Recognizing that such risks cannot be fully eradicated, these standards prioritize governance measures alongside technical safeguards.
|
|
web
|
ukanon.net
|
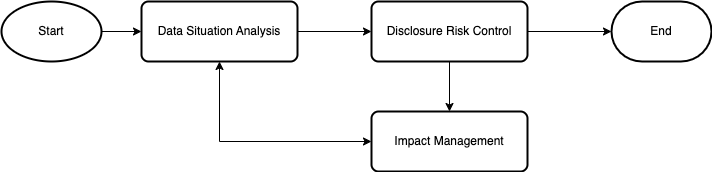
Disclosure risk control starts with risk assessment. Re-Identification risks in a given data environment come from the interaction between agents and data (including the data disclosed/released and other data available to the agents). Thus, both the data risk and the data environment risk (so called context risk) should be assessed. The The governance and infrastructure within the data environment largely determine the likelihood of a certain type of re-identification threats. The assessment can be conducted using either qualitative analysis or quantitative analysis. An initial risk assessment may be required to make a quick decision whether a quantitative risk analysis is needed. (University of Manchester, 2024)
introduces a practical initial risk assessment
tool to help make a decision whether a quantitative risk assessment is needed.
(ISO/IEC 27559, 2022)
specifies an equation for calculating the re-identification risk:
|
|
web
|
dicom.nema.org
|
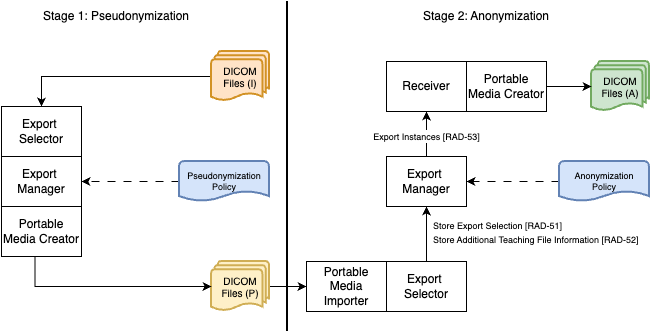
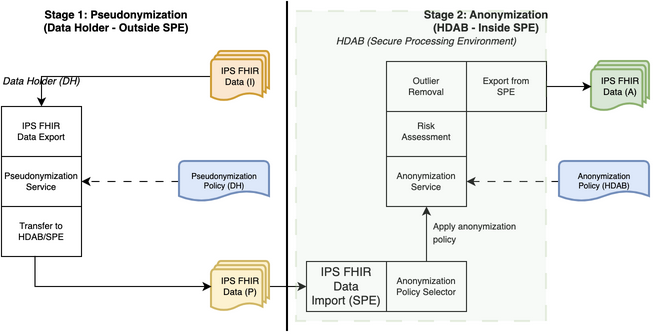
In this example, we assume a dedicated anonymization service is deployed in an environment that serves secondary DICOM use in an environment that is separate from where the medical modality is deployed. The de-identification on the modality usually follows (DICOM PS 3.15, Annex E)
. In this example, we assume the de-identification behavior can be customized as a pseudonymization policy (only processing direct identifiers such as all types of iD/UIDs, patient's id etc). Anonymizing the quasi-identifiers such as patient age will be processed by the dedicated anonymization service, which is based on the TCE profile. The diagram below shows the workflow of the resulting two stages of de-identification. In the diagram, we use the same actor names (export selector, export manager) introduced in the TCE profile just for illustration, meaning the modality does not need to implement their de-identification function by following the transactions required by the TCE profile.
|
|
web
|
github.com
|
The source code for this Implementation Guide can be found on IHE ITI DeIdentification Handbook Github Repo
|
|
web
|
digital.lib.washington.edu
|
It is feasible that motivated individuals who want to target or
embarrass people who have consumed family planning services in
general could compare the de-identified family planning database
with other publicly available databases in order to see how many
individuals can be identified. An excellent analysis of such an
attack on de-identified published Netflix ratings to identify
individual Netflix users is discussed in this paper:
https://digital.lib.washington.edu/dspace-law/bitstream/handle/1773.1/417/vol5_no1_art3.pdf?sequence=1
|
|
web
|
en.npc.gov.cn.cdurl.cn
|
Note 1:
The term is defined in a similar way under the PIPL ( Art. 73(4)
).
|
|
web
|
gdpr-info.eu
|
identifiable natural person
: one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural person. (Source: GDPR Art 4(1)
).
|
|
web
|
www.privacy-regulation.eu
|
Note 2:
The pseudonymised data can no longer be attributed to a specific data subject without the use of additional information, but could be attributed to a natural person by the use of additional information (Source: GDPR Recital 26
).
|
|
web
|
profiles.ihe.net
|
IHE uses the normative words: Shall, Should, and May according to standards conventions
.
|
|
web
|
profiles.ihe.net
|
The use of mustSupport
in StructureDefinition profiles is equivalent to the IHE use of R2
as defined in Appendix Z
.
|
|
web
|
www.iso.org
|
ISO 25237. (2017). Health informatics — Pseudonymization
(ISO 25237:2017; Number ISO 25237:2017). International Organization for Standardization. https://www.iso.org/standard/63553.html
|
|
web
|
www.iso.org
|
ISO/IEC 20889. (2018). Privacy enhancing data de-identification terminology and classification of techniques
(Standard ISO/IEC 20889:2018(E); Number ISO/IEC 20889:2018(E)). International Organization for Standardization. https://www.iso.org/standard/69373.html
|
|
web
|
data.europa.eu
|
GDPR. (2016). Regulation (EU) 2016/679 of the European Parliament and of the Council
. European Parliament and Council of the European Union. https://data.europa.eu/eli/reg/2016/679/oj
|
|
web
|
en.npc.gov.cn.cdurl.cn
|
PIPL. (2021). Personal Information Protection Law of the People’s Republic of China
. National People’s Congress of the People’s Republic of China (NPC). http://en.npc.gov.cn.cdurl.cn/2021-12/29/c_694559.htm
|
|
web
|
doi.org
|
NIST 800-188. (2023). De-identifying Government Datasets
(Special Publication No. 800-188; Numbers 800-188). National Institute of Standards and Technology. https://doi.org/10.6028/nist.sp.800-188
|
|
web
|
www.edpb.europa.eu
|
European Data Protection Board. (2025). Guidelines 01/2025 on Pseudonymisation
. https://www.edpb.europa.eu/system/files/2025-01/edpb_guidelines_202501_pseudonymisation_en.pdf
|
|
web
|
ico.org.uk
|
Information Commissioner’s Office. (2025). Pseudonymisation
. Information Commissioner’s Office. https://ico.org.uk/for-organisations/uk-gdpr-guidance-and-resources/data-sharing/anonymisation/pseudonymisation/#pseudonymiseddatastillpersonal
|
|
web
|
doi.org
|
Hintze, M. (2017). Viewing the GDPR through a de-identification lens: a tool for compliance, clarification, and consistency. International Data Privacy Law
, 8
(1), 86–101. https://doi.org/10.1093/IDPL/IPX020
|
|
web
|
www.iso.org
|
GB/T 42460. (2023). Information security technology - Guide for evaluating the effectiveness of personal information de-identification
(Standard GB/T 42460—2023; Number GB/T 42460—2023). State Administration for Market Regulation Standardization Administration of China. https://www.iso.org/standard/69373.html
|
|
web
|
ukanon.net
|
University of Manchester. (2024). Anonymisation decision-making framework: European practitioners’ guide
(2nd ed.). University of Manchester. https://ukanon.net/wp-content/uploads/2024/01/adf-2nd-edition-european-practitioners-guide-final-version-cover-2024-version-2.pdf
|
|
web
|
dicom.nema.org
|
National Electrical Manufacturers Association. (2025). DICOM Part 15, Annex E: Security and System Management Profiles — Attribute Confidentiality Profiles
(PS3.15 Annex E; Number PS3.15 Annex E). National Electrical Manufacturers Association. https://dicom.nema.org/medical/dicom/current/output/chtml/part15/chapter_E.html
|
|
web
|
www.iso.org
|
ISO/IEC 27559. (2022). Information security, cybersecurity and privacy protection — Privacy enhancing data de-identification framework
(ISO/IEC 27559:2022; Number ISO/IEC 27559:2022). International Organization for Standardization. https://www.iso.org/standard/71677.html
|
|
web
|
www.iso.org
|
ISO/TS 22220. (2011). Health informatics — Identification of subjects of care
(ISO/TS 22220:2011; Number ISO/TS 22220:2011). International Organization for Standardization. https://www.iso.org/standard/44439.html
|
|
web
|
hpl.hp.com
|
HP. Efficient signature schemes supporting redaction, pseudonymization, and data deidentification.
HP.
HPL-2007-191
|
|
web
|
www.schneier.com
|
Schneier, Bruce. Commentary on the Importance of a Systemic Approach to Security.
Bruce Schneier. Essay-028
|
|
web
|
www.nationalarchives.gov.uk
|
UK Redaction Toolkit. A United Kingdom government document describing a toolkit for removing content prior publication for various legal reasons.
REDACTION GUIDELINES FOR THE EDITING OF EXEMPT INFORMATION FROM PAPER AND ELECTRONIC DOCUMENTS PRIOR TO RELEASE
|
|
web
|
www.dicomstandard.org
|
DICOM. DICOM
current publication
|
|
web
|
dicom.nema.org
|
DICOM Part 15 Annex E. Discusses clinical trials, double-blinding, traceability (relinking) to original content, preserving data needed for the trial.
DICOM Part 15, Annex E
current publication
|
|
web
|
healthcaresecprivacy.blogspot.com
|
Moehrke. De-Identification is Highly Contextual
. (2009) De-Identification is highly contextual
|
|
web
|
hitsp.wikispaces.com
|
HITSP. HITSP Biosurveillance Use Case Presentation
. Lists summary of units of data exchange and values that should be pseudonymized. HITSP Biosurveillance Use Case presentation
|
|
web
|
dud.inf.tu-dresden.de
|
Dresden Anonymity. A proposed vocabulary for pseudonymization and related concepts
. Anonymity, Unlinkability, Undetectability, Unobservability, Pseudonymity, and Identity Management – A onsolidated Proposal for Terminology* (Version v0.31 Feb. 15, 2008)
|
|
web
|
web.mit.edu
|
MIT Reidentification. Shows that a large percentage of people can be re-identified with Date-of-Birth, Current ZIP Code, and Sex
. Reidentification of Individuals in Chicago's Homicide Database A Technical and Legal Study
|
|
web
|
www.ema.europa.eu
|
European Medicines Agency. (2025, May 14). External guidance on the implementation of the European Medicines Agency Policy 0070 on the publication of clinical data for medicinal products for human use
(Version 1.5). https://www.ema.europa.eu/en/documents/regulatory-procedural-guideline/external-guidance-implementation-european-medicines-agency-policy-publication-clinical-data-medicinal-products-human-use-version-15_en.pdf
|
|
web
|
www.ipc.on.ca
|
Information and Privacy Commissioner of Ontario. (2016, June). De-identification Guidelines for Structured Data
. https://www.ipc.on.ca/sites/default/files/legacy/2016/08/Deidentification-Guidelines-for-Structured-Data.pdf
|
|
web
|
doi.org
|
Branson, J., Good, N., Chen, JW. et al. (2020). Evaluating the re-identification risk of a clinical study report anonymized under EMA Policy 0070 and Health Canada Regulations. Trials
21, 200. https://doi.org/10.1186/s13063-020-4120-y
|
|
web
|
doi.org
|
Sweeney, L. (2002). k-anonymity: A model for protecting privacy. International Journal on Uncertainty, Fuzziness and Knowledge-Based Systems
, 10(05), 557-570. https://doi.org/10.1142/s0218488502001648
|
|
web
|
doi.org
|
Dwork, C., & Roth, A. (2014). The algorithmic foundations of differential privacy. Foundations and Trends® in Theoretical Computer Science
, 9(3-4), 211-407. https://doi.org/10.1561/0400000042
|
|
web
|
doi.org
|
El Emam, K. (2013). Guide to the de-identification of personal health information
. Auerbach Publications. https://doi.org/10.1201/b14754
|
|
web
|
www.ihe.net
|
IHE provides guidelines for preparing security and privacy risk
assessments in http://www.ihe.net/Technical_Framework/upload/IHE_ITI_Whitepaper_Security_Cookbook_2008-11-10.pdf
|
|
web
|
profiles.ihe.net
|
The act of De-identification, pseudonymization, and re-identification are events that should be logged as part of the Audit Trail and Node Authentication (ATNA)
surveillance log. The specific audit messages that will be appropriate depend upon the usage, and will be profiled elsewhere. The Basic Audit Log Patterns (BALP)
should be reviewed for generalized patterns of ATNA audit log messages and some specific privacy events.
|
|
web
|
en.wikipedia.org
|
In statistics, a categorical variable (also called qualitative variable) is a variable that can take on one of a limited, and usually fixed, number of possible values, assigning each individual or other unit of observation to a particular group or nominal category on the basis of some qualitative property. Source: Wikipedia
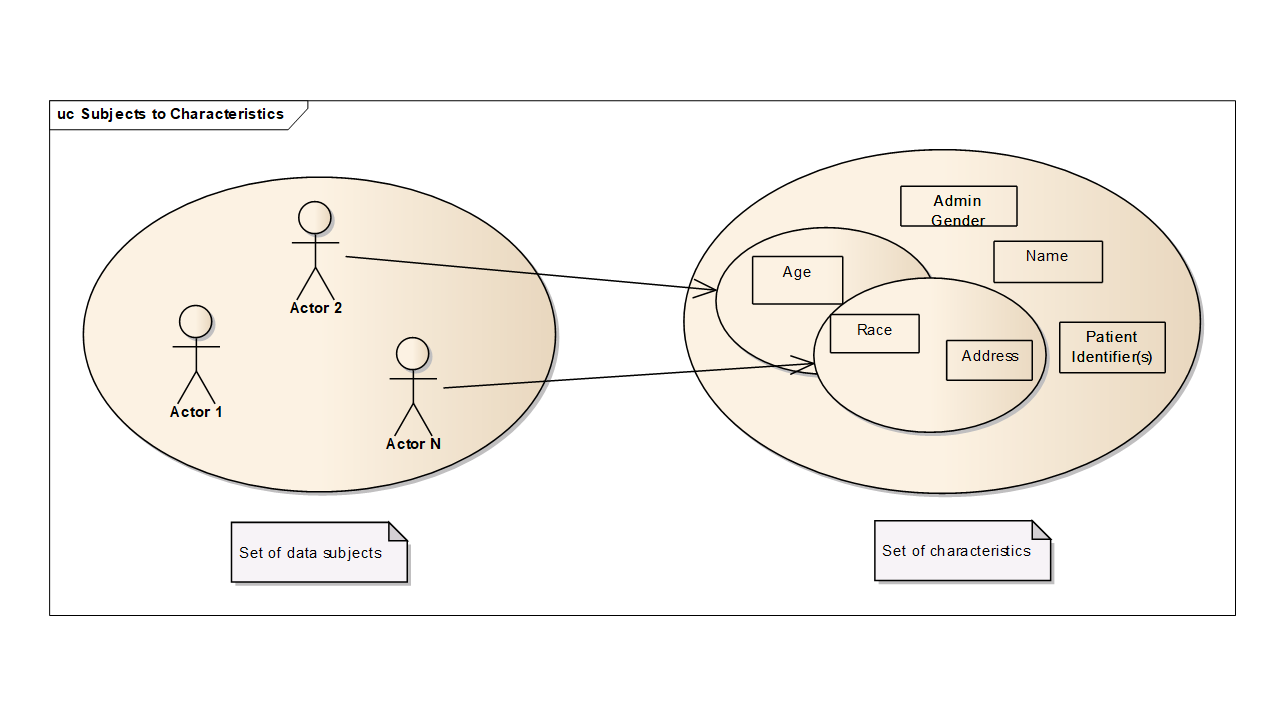
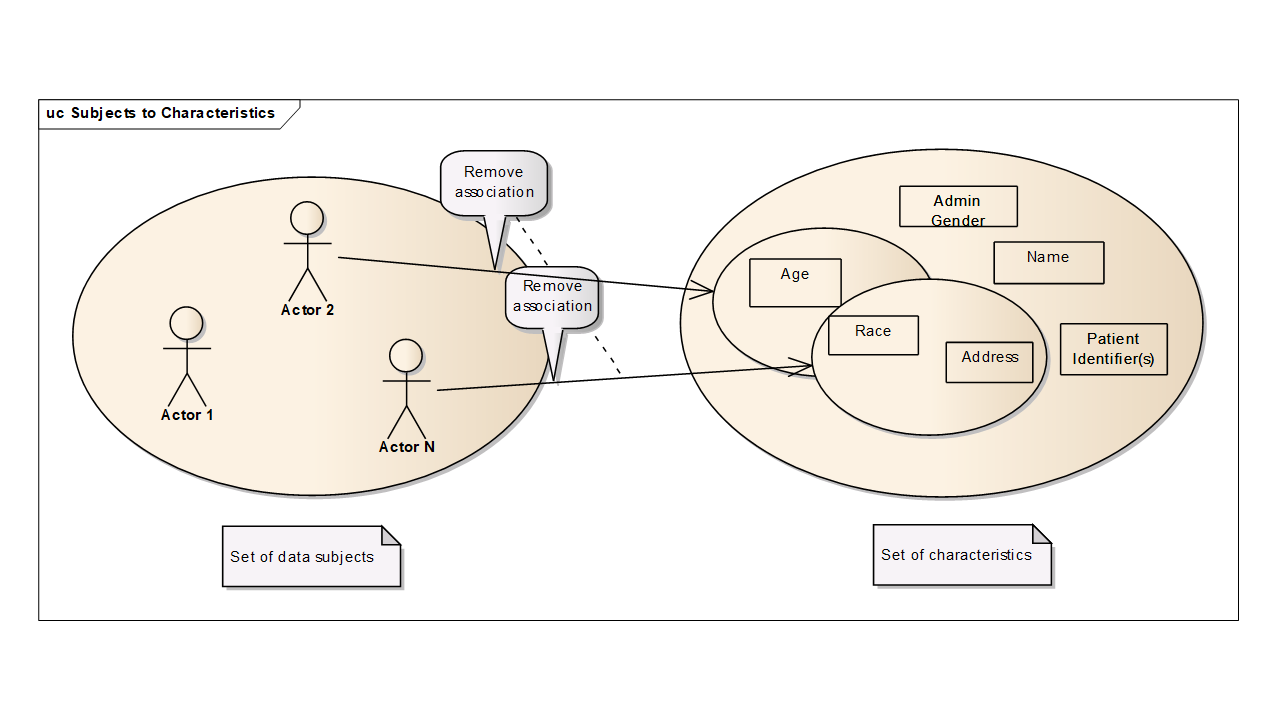
. In the context of de-identification, categorical quasi-identifiers are categorical variables. In healthcare, patient gender, diagnostic code are typical examples of categorical quasi-identifiers.
|