This fragment is available on downloads.html
This publication includes IP covered under the following statements.
| Type | Reference | Content |
|---|---|---|
| web | github.com | FHIR Data Segmentation for Privacy, published by HL7 Security Working Group. This guide is not an authorized publication; it is the continuous build for version 1.0.0 built by the FHIR (HL7® FHIR® Standard) CI Build. This version is based on the current content of https://github.com/HL7/fhir-security-label-ds4p/ and changes regularly. See the Directory of published versions |
| web | www.itu.int | The combination of a hierarchical security classification and a security category that represents the sensitivity of an object or the security clearance of an individual [ ISO 2382-8 ]. |
| web | www.itu.int | The portion (possibly all) of the ACI made available to the ADF in making a particular access control decision [ ISO 10181-3/ITU X.812 ]. |
| web | www.itu.int | Any information used for access control purposes, including contextual information [ ISO 10181-3 ]. |
| web | www.astm.org | Confidential protection of data elements by segmentation into restricted and specifically controlled categories set by policies [Adapted from ASTM E1986-98(2005) ]. |
| web | www.itu.int | Initiator-bound access control information (ACI) that can be compared with security labels of targets [ ISO 10181-3/ITU X.812 ]. |
| web | www.itu.int | Permission granted to an individual to access data or information at or below a particular security level [ ISO/IEC 2382-8:1998 ]. |
| web | www.itu.int | A division of data into isolated blocks with separate security controls for the purpose of reducing risk [ ISO 7498-2 ]. For example, the division of data in a major project into blocks corresponding to sub-projects, each with its own security protection, in order to limit exposure of the overall project. |
| web | www.iso.org | If present, the privacy-mark is not used for access control. The content of the privacy-mark may be defined by the security policy in force (identified by the security-policy-identifier) which may define a list of values to be used. Alternately, the value may be determined by the originator of the security-label [ ISO 22600-3 Section A.3.4.3]. |
| web | www.iso.org | The information that documents the history of the Content Information. This information tells the origin or source of the Content Information, any changes that may have taken place since it was originated, and who has had custody of it since it was originated. The archive is responsible for creating and preserving Provenance Information from the point of Ingest; however, earlier Provenance Information should be provided by the Producer. Provenance Information adds to the evidence to support Authenticity [ ISO 14721 ]. |
| web | docs.oasis-open.org | Characteristic of a subject, resource, action or environment that may be referenced in a predicate or target [ XACML ]. |
| web | www.itu.int | A non-hierarchical grouping of sensitive information used to control access to data more finely than with hierarchical security classification alone [ ISO 2382-8 ]. |
| web | fismapedia.org | The characterization of information or an information system based on an assessment of the potential impact that a loss of confidentiality, integrity, or availability of such information or information system would have on organizational operations, organizational assets, or individuals [ FIPS ]. |
| web | www.iso.org | If present, the security categories provide further granularity for the sensitivity of the message. The security policy in force is used to indicate the syntaxes that are allowed to be present in the security-categories. Alternately, the security-categories and their values may be defined by bilateral agreement [ ISO 22600-3 Section A.3.4.3]. |
| web | www.itu.int | The determination of which specific degree of protection against access the data or information requires, together with a designation of that degree of protection; for example, “Top Secret”, “Secret”, “Confidential” [ ISO 2382-8 ]. |
| web | www.itu.int | The means used to associate a set of security attributes with a specific information object as part of the data structure for that object [ ISO 10181-3/ITU X.812 ]. |
| web | www.itu.int | Access control information associated with the attribute values being accessed [ ISO/IEC 9594-2:2008/ITU X.501 ]. |
| web | www.itu.int | The marking bound to a resource (which may be a data unit) that names or designates the security attributes of that resource. NOTE - The marking and/or binding may be explicit or implicit [ ISO 7498-2 ]. |
| web | www.itu.int | Security labels may be used to associate security-relevant information with attributes within the Directory. Security labels may be assigned to an attribute value in line with the security policy in force for that attribute. The security policy may also define how security labels are to be used to enforce that security policy. A security label comprises a set of elements optionally including a security policy identifier, a security classification, a privacy mark, and a set of security categories. The security label is bound to the attribute value using a digital signature or other integrity mechanism [ ISO/IEC 9594-2:2008/ITU X.501 ]. |
| web | xmpp.org | A security label, sometimes referred to as a confidentiality label, is a structured representation of the sensitivity of a piece of information. A security label is used in conjunction with a clearance, a structured representation of what information sensitivities a person (or other entity) is authorized to access and a security policy to control access to each piece of information [ XMPP Core ]. |
| web | www.itu.int | A construct that conveys domain-specific security policy information [ ISO/IEC 15816 ]. |
| web | www.xmlspif.org | An XML schema, that provides a high level representation of a security labeling policy in a generic and open fashion [ Open XML SPIF ]. |
| web | www.iso.org | ISO/IEC 15816:2002 Information technology — Security techniques — Security information objects for access control |
| web | www.itu.int | The characteristic of a resource which implies its value or importance and may include its vulnerability [ ISO/IEC 7498-2 ]. |
| web | www.faqs.org | Security labels which support data confidentiality models, like the Bell and LaPadula model. The sensitivity label tells the amount of damage that will result from the disclosure of the data and also indicates which measures the data requires for protection from disclosure. The amount of damage that results from unauthorized disclosure depends on who obtains the data; the sensitivity label should reflect the worst case [ IETF RFC 1457 ]. |
| web | www.iso.org | Sets of rules followed by the parties involved for achieving interoperability [ ISO 22600-2 ]. |
| web | www.iso.org | Policy that rules the behavior of a system. The Trust Framework facilitates trustworthy co-operation between domains by defining a common set of security and privacy policies that applies to all collaborating entities, derived from the relevant domain-specific policies across all of those policy domains [ ISO 22600-2 ]. |
| web | www.hl7.eu | The HL7 V2 security label guidance is incorporated in HL7 Version 2.9, Chapter 3, Patient Administration Access Control Restriction Value Segment (ARV) , and the Chapter 2 Control description of the Batch Header Segment (BHS) , the File Header Segment (FHS) , and the Message Header Segment (MSH) . |
| web | www.hl7.eu | The HL7 V2 security label guidance is incorporated in HL7 Version 2.9, Chapter 3, Patient Administration Access Control Restriction Value Segment (ARV) , and the Chapter 2 Control description of the Batch Header Segment (BHS) , the File Header Segment (FHS) , and the Message Header Segment (MSH) . |
| web | www.hl7.eu | The HL7 V2 security label guidance is incorporated in HL7 Version 2.9, Chapter 3, Patient Administration Access Control Restriction Value Segment (ARV) , and the Chapter 2 Control description of the Batch Header Segment (BHS) , the File Header Segment (FHS) , and the Message Header Segment (MSH) . |
| web | www.hl7.eu | The HL7 V2 security label guidance is incorporated in HL7 Version 2.9, Chapter 3, Patient Administration Access Control Restriction Value Segment (ARV) , and the Chapter 2 Control description of the Batch Header Segment (BHS) , the File Header Segment (FHS) , and the Message Header Segment (MSH) . |
| web | www.law.cornell.edu |
implementation of the CDA DS4P IG at the Header Level was included as an optional Certified EHR Certification criteria in the original 2015 Edition Health Information Technology (Health IT) Certification Criteria, 45 CFR § 170.315 - 2015 Edition Health IT Certification Criteria and ONC Health IT Certification Program Modifications ( Final Rule – October 16, 2015 ). |
| web | www.law.cornell.edu | In 21st Century Cures Act: Interoperability, Information Blocking, and the ONC Health IT Certification Program , the ONC revised the security tag certification criteria in 45 CFR § 170.315 - 2015 Edition health IT certification criteria at (b)(7) and (b)(8) by requiring certification at the more granular Section and Entry levels after December 31, 2022. |
| web | fismapedia.org | Generally, a Security Label is assigned in accordance with a policy, which deems an aspect of a valued information object warrant a level of confidentiality protection. The policy is based on an assessment of the potential impact that a loss of confidentiality, integrity, or availability of such information or information system would have on organizational operations, organizational assets, or individuals (this definition of Security Category is used in a number of NIST publications, which are listed here ). |
| web | www.iso.org | Information Sensitivity is the characteristic of an IT resource which implies its value or importance and may include its vulnerability [ISO 7498-2] . Along with any relevant policy, information sensitivity is a strong determinant of the required level of confidentiality protection. |
| web | www.law.cornell.edu | Restricted : The “restricted” confidentiality code applies when a narrower policy domain preempts the “normative” level of protection in a wider policy domain (e.g., HIPAA in US, GDPR in EU) of sensitive information within the context of healthcare delivery. Examples in the US include State behavioral health, reproductive health, minors’ health, and HIV laws, Medicaid Confidentiality, Title 38 Section 7332 , 42 CFR Part 2 , and terms and conditions of federal grant programs such as community health centers ( 42 CFR 51c.110 ) and the Title X Program. |
| web | www.law.cornell.edu | Restricted : The “restricted” confidentiality code applies when a narrower policy domain preempts the “normative” level of protection in a wider policy domain (e.g., HIPAA in US, GDPR in EU) of sensitive information within the context of healthcare delivery. Examples in the US include State behavioral health, reproductive health, minors’ health, and HIV laws, Medicaid Confidentiality, Title 38 Section 7332 , 42 CFR Part 2 , and terms and conditions of federal grant programs such as community health centers ( 42 CFR 51c.110 ) and the Title X Program. |
| web | www.law.cornell.edu | Restricted : The “restricted” confidentiality code applies when a narrower policy domain preempts the “normative” level of protection in a wider policy domain (e.g., HIPAA in US, GDPR in EU) of sensitive information within the context of healthcare delivery. Examples in the US include State behavioral health, reproductive health, minors’ health, and HIV laws, Medicaid Confidentiality, Title 38 Section 7332 , 42 CFR Part 2 , and terms and conditions of federal grant programs such as community health centers ( 42 CFR 51c.110 ) and the Title X Program. |
| web | www.iso.org | Per ISO 22600-3 (Section A.3.4.3) , privacy marks are not used for access control. The content of the privacy-mark may be defined by the security policy in force (identified by the security-policy-identifier) which may define a list of values to be used. Alternately, the value may be determined by the originator of the security-label. |
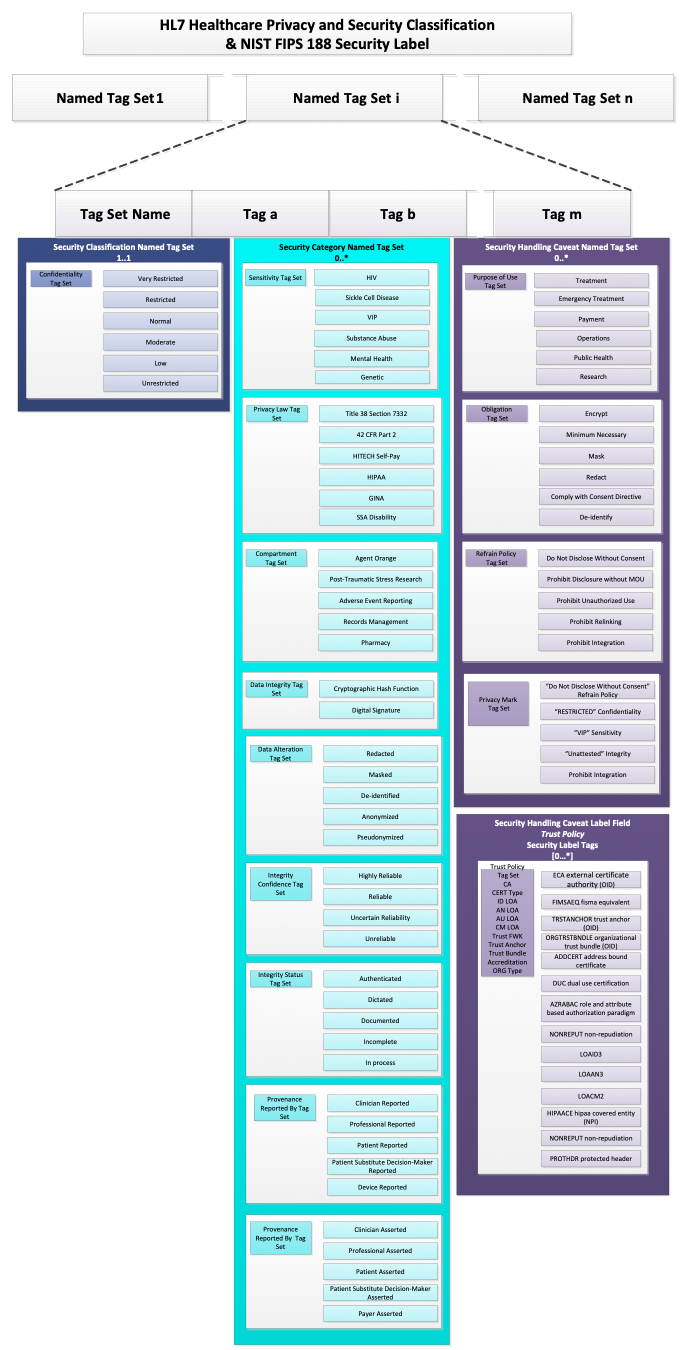
hcs-example.png 
|
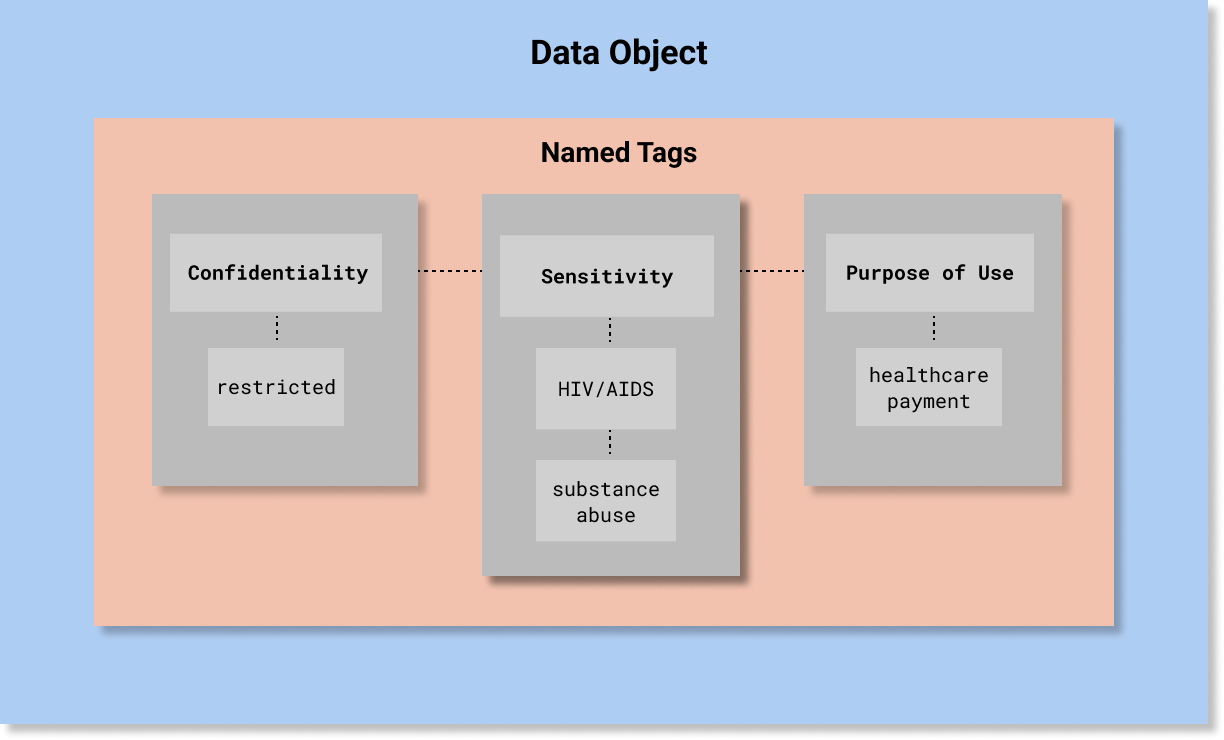
hcs-label-example.png 
|
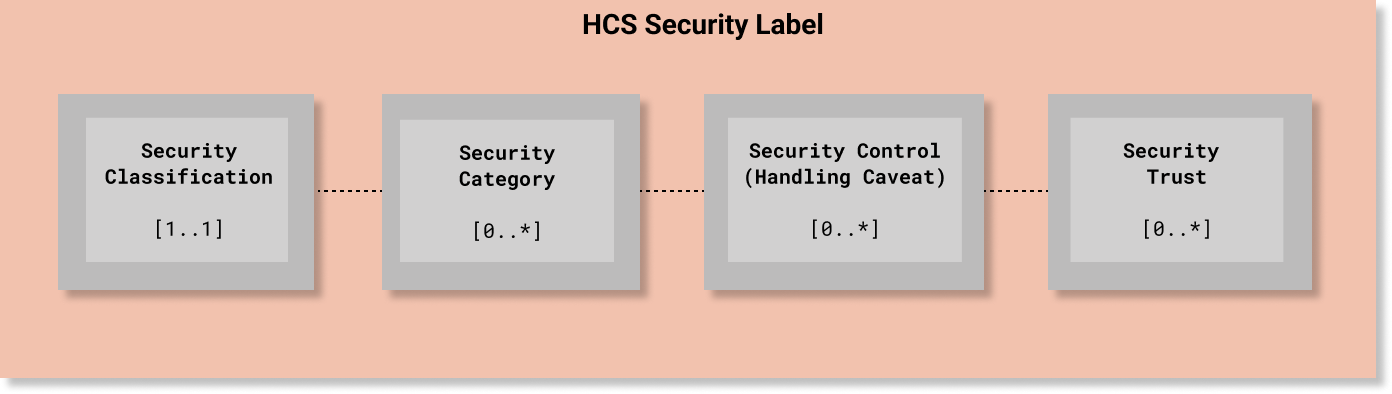
hcs-label.png 
|
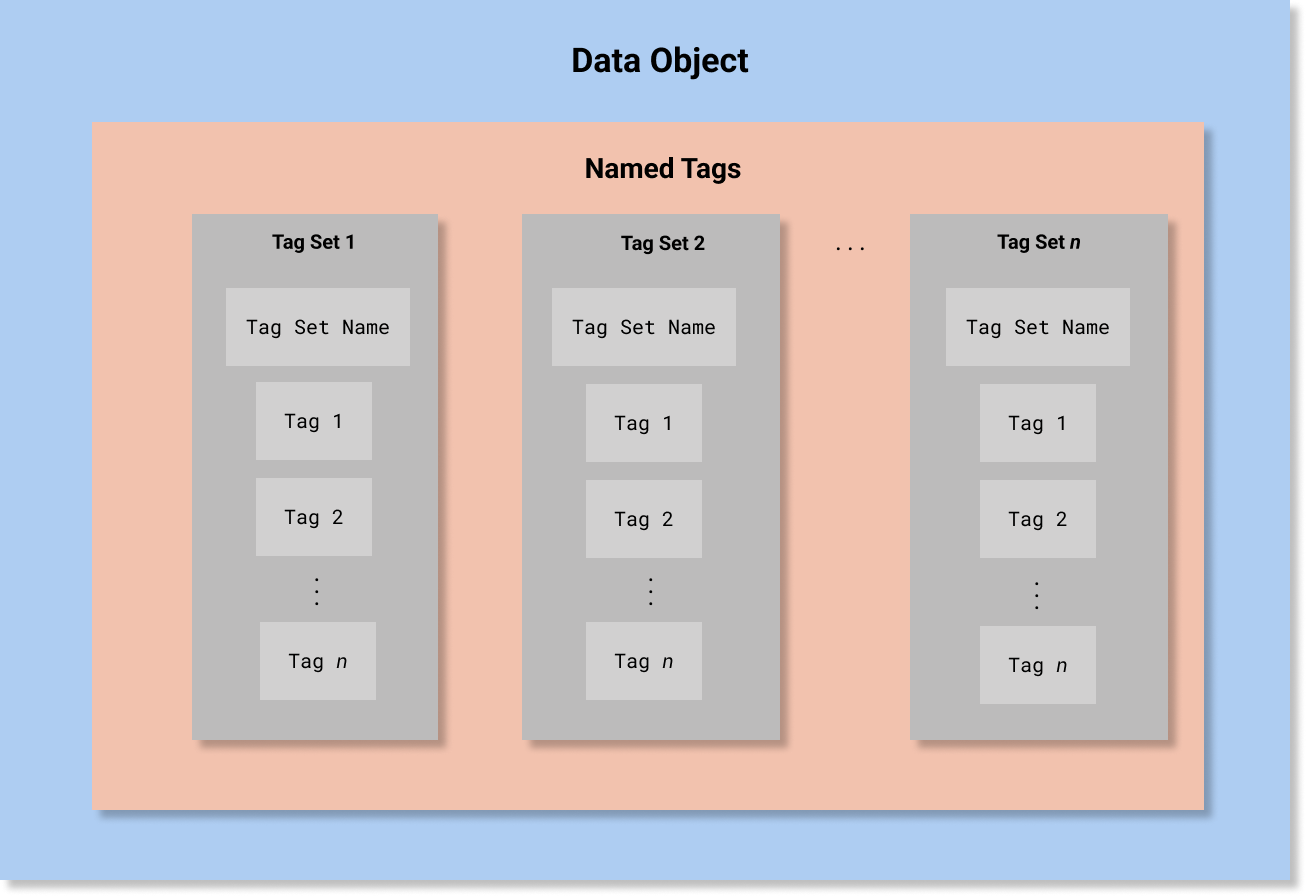
named-tagset.png 
|
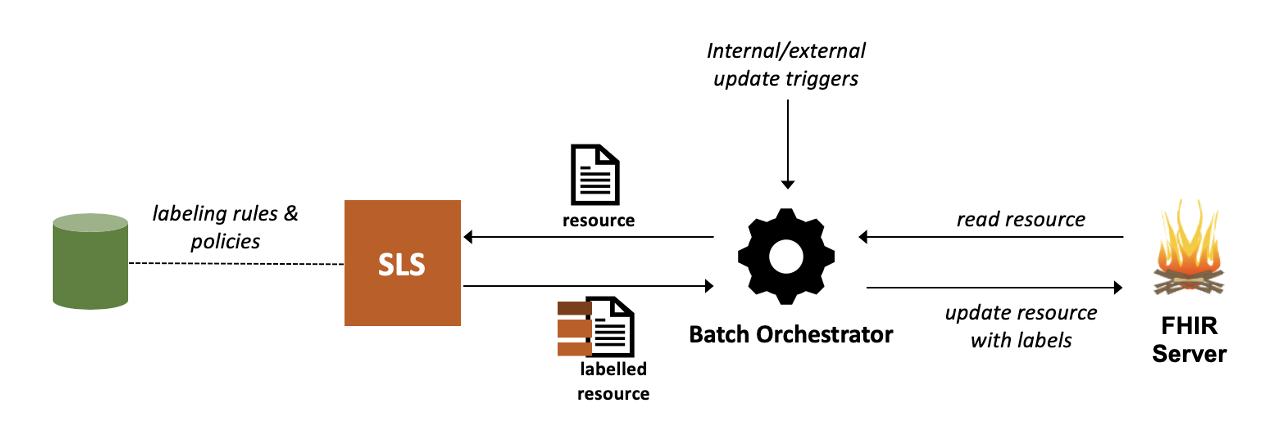
sls-batch.png 
|
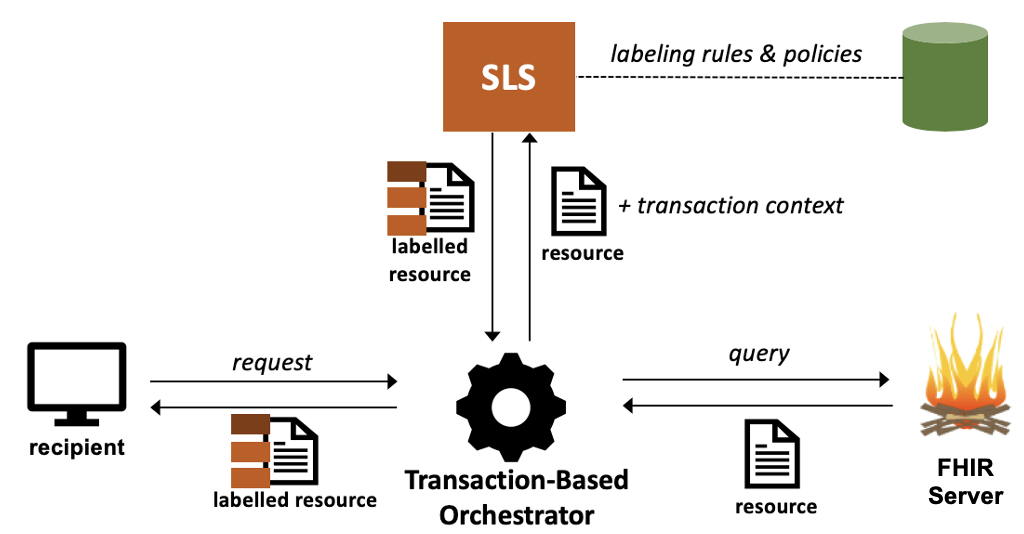
sls-transaction.png 
|
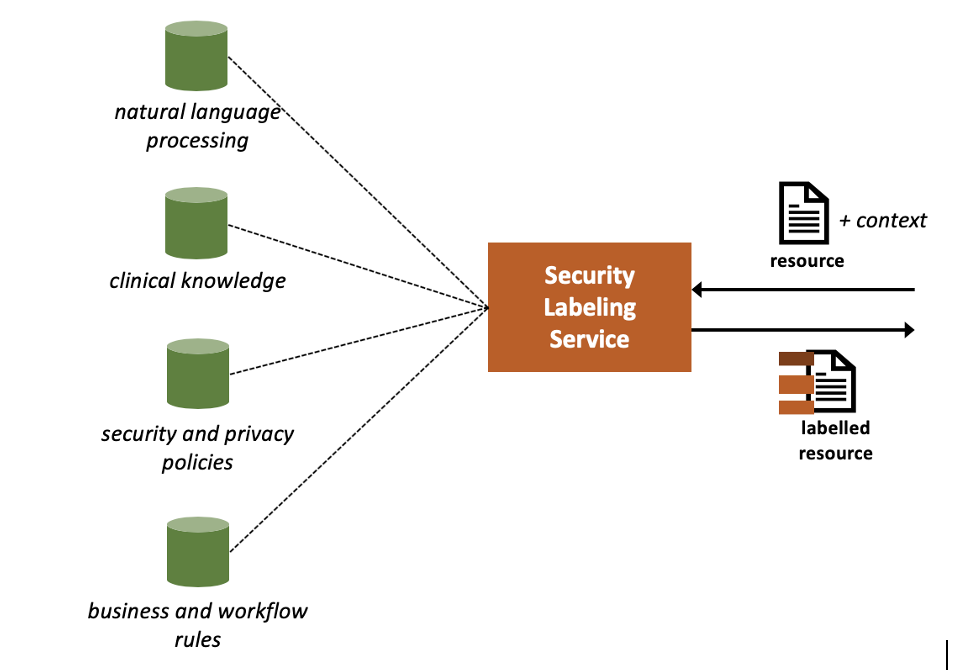
sls.png 
|